Numerous radio-frequency identification (RFID) applications are implemented in various sectors for very different purposes. Conventional examples include automatic electronic tracking of goods in supply chains, cashless payments and physical building access with an electronic card.
Non-traditional applications apply the ubiquitous and permeative nature of RFID in new ways. Specifically, RFID is being used as an interface embedded throughout the environment for data collection or for seamlessly calling for services and information. Recent RFID applications exploit the inexpensive and miniature form factor of RFID tags to sync real and virtual worlds.
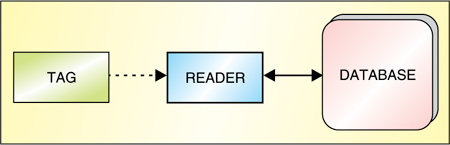
RFID readers collect data wirelessly from electronic transponders, also called tags, which are attached to or embedded in objects. RFID systems are built around software, networks and databases that enable information to flow from tags to the infrastructure where it is processed and stored.
RFID systems are created to suit the intended application. Some use low-cost passive tags, which have low data capacity and also short read range. Most data is put on the network, and only a small amount of information is loaded onto tags. Others use sophisticated, high-performance tags with high read ranges. These may store considerable data on tags, without network connection.
Roots of RFID
RFID has been dubbed the world’s oldest new technology. It dates back to the 19th century with applications related to friend or foe identification of military aircrafts. The ‘identify friend or foe’ (IFF) system allowed radar operators and pilots to automatically distinguish a friendly aircraft from enemies’ via radio-frequency signals. IFF systems helped prevent ‘friendly fire’ incidents and assisted in intercepting the enemy aircrafts. The first commercial applications appeared in the 1960s in the area of electronic article surveillance to fight against product theft—an application that is still widely used today.
Automatic object detection systems preceded automatic RFID systems. According to the Handbook of Technology Management, one of the earliest patented systems was a radio transmitter for object detection system designed by John Logie Baird in 1926. The passive communication technology often used in RFID was first presented in Henry Stockman’s seminal paper ‘Communication by Means of Reflected Power’ in 1948.
RFID applications
There are many kinds of RFID systems used in different applications and settings. These systems have different power sources, operating frequencies and functionality.
At the core, RFID systems consist of small transponders (tags) attached to physical objects. When queried by RFID transceivers (readers), tags respond with some unique identifying information that may be associated with arbitrary data records. Thus RFID systems are a type of automatic identification (Auto- ID) system, similar to optical bar codes. However, Auto-ID systems that transmit data via radio signals do not have the same performance limitations as optical systems— according to Handbook of Technology Management.
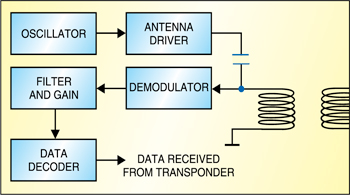
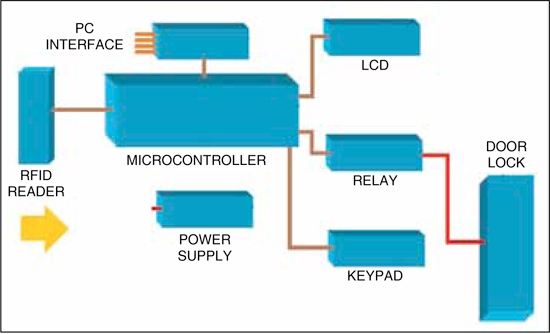
RFID system requisites
Common applications of RFID systems include tracking and access control. Robert Weiss, in his book RFID: Principles and Application, says that a standard RFID system consists of at least three core components:
1. RFID tags (transponders), which carry object-identifying data
2. RFID readers (transceivers), which read and write tag data
3. Databases, which associate tag-identifying data with arbitrary records
The basic function of an RFID system is identification. When queried by a reader, tags return an identifier that may be used to retrieve other data records. The tag is attached to the object to be identified.
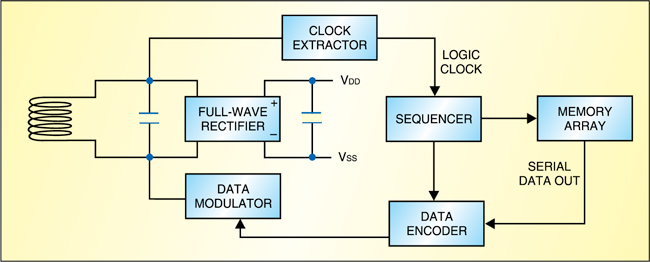
Typically, the tags consist of an antenna and an electronic circuit. Often, these carry no on-board battery (passive tags) and must harvest all energy from the RF signal. Newer tags tend to implement identification functionality on a chip (IC) that provides computation and storage. In the manufacturing process, this tiny chip is attached to an antenna before being packaged in a form factor (glass capsule or foil) inlay, which is integrated into the finished product.

The reader communicates with the tag through a radio-frequency channel to obtain the identifying information. Depending on the type of tag, this communication may be a simple ping or a more complex multi-round protocol.
Readers come in many forms, operate on many different frequencies and may offer a wide range of functionality. These may have their own processing power and internal storage, and may offer network connectivity. Readers might be a simple conduit to an external system or store all relevant data locally. Databases are assumed to have a secure connection to readers.
Presence sensing and building access control
RFID proximity cards (Prox Cards) are widely used for presence sensing and building access control throughout the world. These are passive tags with no on-board battery, relying solely on a reader to operate. Usually, passive tags do not have their own power source or the ability to initiate communication. These obtain energy from incoming RF signals by induction. Often, the reader energises the tag through the RF channel.