RFID technology allows non-contact transfer of information (much like the familiar barcode), making it effective in manufacturing and other hostile environments where barcode labels could not survive. Take a look at how it works and what are its pros and cons.
Radio-frequency identification (RFID) technology involves the use of electromagnetic or electrostatic coupling in the RF portion of the electromagnetic spectrum to uniquely identify an object, animal or person. It has established itself in a wide range of markets including livestock identification and automated vehicle identification because of its ability to track moving objects. The technology has also become a primary component of automated data collection, identification and analysis systems worldwide.
Architecture and working of RFID
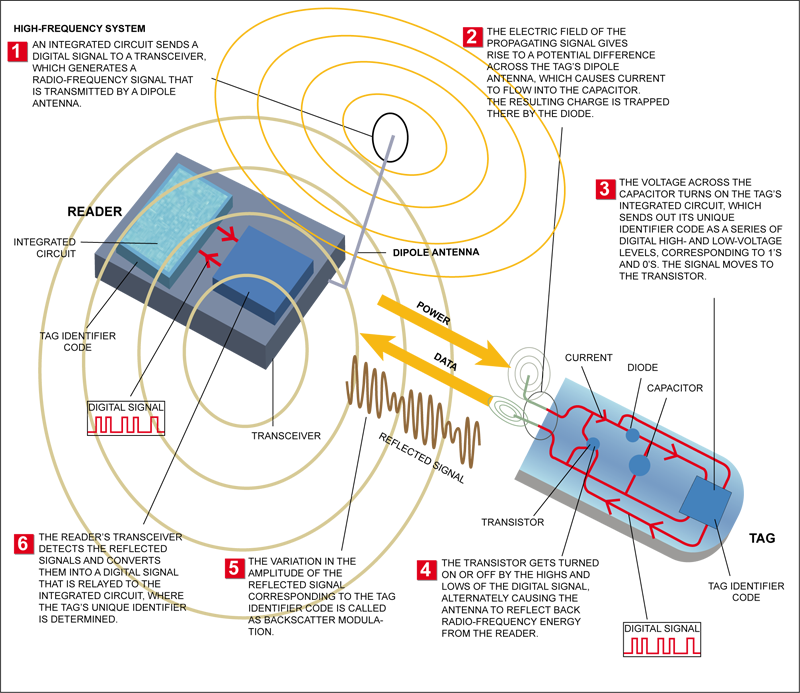
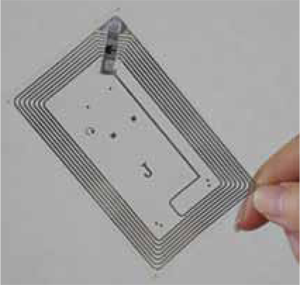
An RFID system consists of three components: a transceiver (often combined into the reader), some sort of data processing equipment, such as a computer, and a transponder (the tag). A typical RFID system is shown in Fig. 1.
RFID tag
RFID tag, usually known as transponder, acts as a transmitter as well as a receiver in the RFID system. The three basic components of the RFID tag are an antenna, a microchip (memory) and the encapsulating material.
 In a typical system, tags are attached to objects. Each tag has a certain amount of internal memory (EEPROM) in which it stores information about the object, such as its unique ID (serial) number, or in some cases more details including manufacture date and product composition.
In a typical system, tags are attached to objects. Each tag has a certain amount of internal memory (EEPROM) in which it stores information about the object, such as its unique ID (serial) number, or in some cases more details including manufacture date and product composition.
When these tags pass through a field generated by a reader, they transmit this information back to the reader, thereby identifying the object. The antenna uses radio frequency waves to transmit a signal that activates the transponder. When activated, the tag transmits data back to the antenna. The data is used to notify a programmable logic controller that an action should be taken. The action could be as simple as raising an access gate or as complicated as interfacing with a database to carry out a monetary transaction.
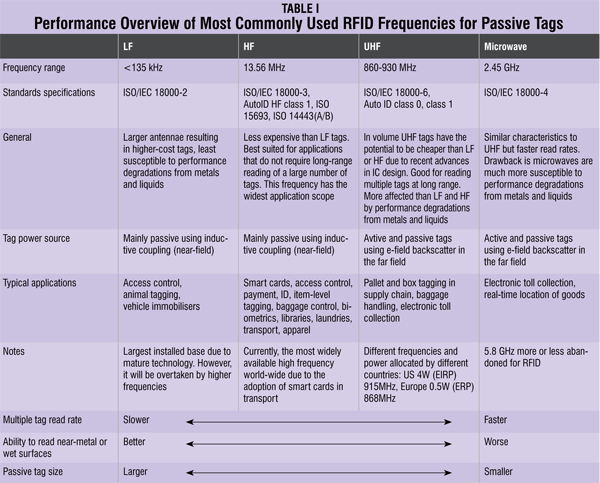
Low-frequency (30-500 kHz) RFID systems have a short transmission range (generally less than 1.8 metres). High-frequency (850-950 MHz and 2.4-2.5 GHz) RFID systems offer a longer transmission range (more than 27 metres). In general, the higher the frequency, the more expensive the system. RFID is sometimes called dedicated short-range communication.
There are two types of RFID tags
Read-only tag and read-write tag. In the read-only tag, the microchip or memory is written only once, during manufacturing process. The information, along with the serial number on the read-only tag, can never be changed. In the read-write tag, only the serial number is written during manufacturing process. The remaining blocks can be re-written by the user.
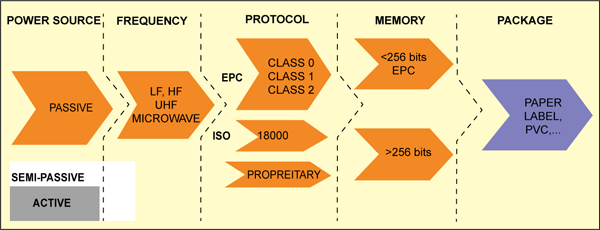
Until recently, the focus of RFID technology was mainly on tags and readers which were being used in systems involving relatively low volumes of data. This is now changing as RFID in the supply chain is expected to generate huge volumes of data, which will have to be filtered and routed to the backend IT systems. To solve this problem, companies have developed special software packages called savants, which act as buffers between the RFID front-end and the IT backend. Savants are equivalent to middleware in the IT industry.
RFID reader
RFID reader is the device used to transmit to and receive information from the RFID tag. It is also referred to as an ‘interrogator.’ It includes sensors that read the RFID tags in the vicinity.
The reader sends a request for information to the tag. The tag responds with the respective information, which the reader then forwards to the data processing device. The tag and reader communicate with one another over a radio frequency channel. In some systems, the link between the reader and the computer is wireless.
Supporting infrastructure. The supporting infrastructure includes related software and hardware required for RFID systems. The software manages the interaction between the RFID reader and the RFID tags.
Communication protocol
The communication process between the reader and tag is managed and controlled by one of several protocols, such as the ISO 15693 and ISO 18000-3 for HF, or the ISO 18000-6 and EPC 18000-6 for UHF. Basically, when the reader is switched on, it starts emitting a signal at the selected frequency band (typically 860-915 MHz for UHF or 13.56 MHz for HF). Any corresponding tag in the vicinity of the reader will detect the signal and use the energy from it to wake up and supply operating power to its internal circuits. Once the tag has encoded the signal as valid, it replies to the reader, and indicates its presence by modulating (affecting) the reader field.
Anti-collision
If many tags are present, they will all reply at the same time. At the reader end, this is seen as signal collision and an indication of multiple tags. The reader manages this problem by using an anti-collision algorithm that allows tags to be sorted and individually selected. There are many different types of algorithms (binary tree, aloha, etc) which are defined as part of the protocol standards.
The number of tags that can be identified depends on the frequency and protocol used, and can typically range from 50 tags/s for HF to 200 tags/s for UHF. Once a tag is selected, the reader is able to perform a number of operations such as reading the tags. This process continues under control of the anti-collision algorithm until all the tags have been selected.
Inductively coupled RFID tags
These original tags were complex systems of metal coils, antennae and glass. Inductively coupled RFID tags were powered by a magnetic field generated by the RFID reader. Electrical current has an electrical component and a magnetic component, i.e., it is electromagnetic. The name ‘inductively coupled’ comes from the magnetic field inducted by a current in the wire.
Pros of RFID Tags
- RFID tags are rugged and robust and can work in harsh temperatures and environment. The RFID system works at a remarkably high speed, even in adverse conditions.
- RFID tags are available in different shapes, sizes, types and materials. The information on the read-only tag cannot be altered or duplicated. Read-write tags can be used repeatedly. The RFID tags are always read without any error.
- Direct physical contact between the tags and the reader is not required. RF technology is used for communication.
- Multiple RFID tags can be read at the same time. The RFID tags can be read in a bulk of ten to 100 tags at a time. Reading of the tags is automatic and involves no labour.
- RFID systems can identify and track unique items, unlike the bar code system which identifies only the manufacturer and the product type.
- The entire RFID system is very reliable, which allows the use of RFID tags for security purpose.
- The storage capacity of the RFID tags is greater than of any other automatic identification and tracking system.
Cons of RFID Tags
- The RFID system is costly compared to other automatic identification systems. The cost can increase further if the RFID system is designed for a specific application.
- Size and weight of the tags is more as compared to barcode system. The electronic components like antenna, memory and other parts of the tags make them bulky.
- Although the tags work in harsh environments, the signals from certain types of tags get affected when they come in close contact with certain metals or liquids. Reading such tags becomes difficult and sometimes the data read is erroneous.
- There is no way in which damaged tags can be tracked and replaced with tags that are intact.
- Although the tags do not require line-of-sight communication, they can be read within a specified range only.
Capacitively coupled tags
These tags were created to lower the technology’s cost. These were disposable tags that could be applied to less expensive merchandise and made as universal as bar codes. Capacitively coupled tags used conductive carbon ink instead of metal coils to transmit data. The ink was printed on paper labels and scanned by readers.
Motorola’s BiStatix RFID tags
These were the frontrunners in this technology. They used a silicon chip that was only 3 millimetres wide and stored 96 bits of information. This technology didn’t catch on with retailers, and BiStatix was shut down in 2001.
Inductively coupled and capacitively coupled RFID tags aren’t used as commonly today because these are expensive and bulky. Newer innovations in the RFID industry include active, semi-active and passive RFID tags. These tags can store up to 2 kilobytes of data and are composed of a micro-chip, antenna and, in the case of active and semi-passive tags, a battery. The tag’s components are enclosed within plastic, silicon or sometimes glass. Table I gives the performance overview of the different-frequency passive tags.
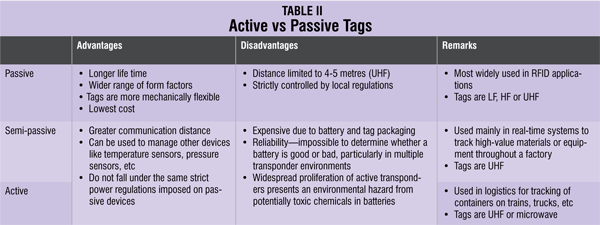
Active and passive tags
The first basic choice when considering a tag is between passive, semi-passive and active. Passive tags can be read from a distance of up to 4-5 metres using the UHF frequency band, whilst the other types of tags (semi-passive and active) can achieve much greater communication distances of up to 100 metres for semi-passive and several kilometres for active. This large difference in communication performance can be explained by the following:
- Passive tags use the reader field as a source of energy for the chip and for communication from and to the reader. The available power from the reader field not only reduces very rapidly with distance but is also controlled by strict regulations, resulting in a limited communication distance of 4-5 metres when using the UHF frequency band (860-930 MHz).
- Semi-passive (battery-assisted backscatter) tags have built-in batteries and therefore do not require energy from the reader field to power the chip. This allows them to function with much lower signal power levels, resulting in greater distances of up to 100 metres. Distance is limited mainly because the tag does not have an integrated transmitter, and still has to use the reader field to communicate back to the reader.
- Active tags are battery-powered devices that have an active transmitter onboard. Unlike passive tags, these generate RF energy and apply it to the antenna. This autonomy from the reader means that they can communicate from distances of over several kilometres.
HF and UHF are best suited to the supply chain. UHF, due to its superior read range, will become the dominant frequency. LF and microwave will not be used in certain cases.
Tag Ics
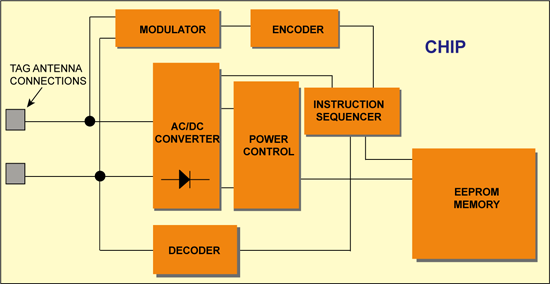
RFID tag ICs are designed and manufactured using some of the most advanced and smallest-geometry silicon processes available. The result is impressive, when you consider that the size of a UHF tag chip is around 0.3 mm2.
In terms of computational power, RFID tags are quite dumb, containing only basic logic and state machines capable of decoding simple instructions. This does not mean that they are simple to design. In fact, very real challenges exist such as achieving very low power consumption, managing noisy RF signals and keeping within strict emission regulations.
Other important circuits allow the chip to transfer power from the reader signal field, and convert it via a rectifier into a supply voltage. The chip clock is also normally extracted from the reader signal.
The amount of data stored on a tag depends on the chip specifications, and can range from just simple identifier numbers of around 96 bits to more information about the product containing up to 32 kbits. However, greater data capacity and storage (memory size) leads to larger chip sizes and hence more expensive tags.
In 1999, the AUTO-ID Center (now EPC Global) based at the Massachusetts Institute of Technology in the US, together with a number of leading companies, developed the idea of a unique electronic identifier code called the electronic product code (EPC). The EPC is similar in concept to the universal product code used in barcodes today.
Having just a simple code of up to 256 bits would lead to smaller chip size and hence lower tag costs, which is recognised as the key factor for widespread adoption of RFID in the supply chain. Tags that store just an ID number are often called licence plate tags.
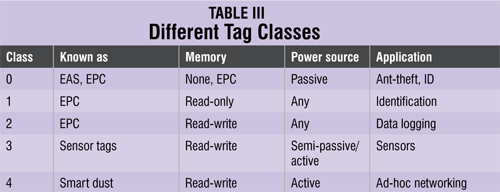
Tag classes
One of the main ways of categorising RFID tags is by their capability to read and write data. This leads to the following four classes:
Class 0 (read-only, factory-programmed)
These are the simplest type of tags, where the data, which is usually a simple ID number (EPC), is written only once into the tag during manufacture. The memory is then disabled from any further updates. Class 0 is also used to define a category of tags called electronic article surveillance or anti-theft devices, which have no ID and announce their presence only when passing through an antenna field.
Class 1 (write-once read-only, factory- or user-programmed)
In this case, the tag is manufactured with no data written into the memory. Data can then either be written by the tag manufacturer or by the user one time. Following this no further writes are allowed and the tag can only be read. Tags of this type usually act as simple identifiers.
Class 2 (read-write)
These are the most flexible type of tags, where users have access to read and write data into the tag’s memory. They are typically used as data loggers and therefore contain larger memory space than what is needed for just a simple ID number.
Class 3 (read-write with on-board sensors)
These tags contain on-board sensors for recording parameters like temperature, pressure and motion by writing into the tag’s memory. As sensor readings must be taken in the absence of a reader, the tags are either semi-passive or active.
Class 4 (read-write with integrated transmitters)
These are like miniature radio devices which can communicate with other tags and devices without the presence of a reader. This means that they are completely active with their own battery power source.
Selecting a tag
Choosing the right tag for a particular RFID application is an important consideration, and should take into account many of the factors listed below:
- Size and form factor—where does the tag have to fit?
- How close will the tags be to each other?
- Durability—does the tag need to have a strong outer protection against regular wear and tear?
- Is the tag reusable?
- Resistance to harsh (corrosive, steamy, etc) environments
- Polarisation—the tag’s orientation with respect to the reader field
- Exposure to different temperature ranges
- Communication distance
- Influence of materials such as metals and liquids
- Environment (electrical noise, other radio devices and equipment)
- Operating frequency (LF, HF or UHF)
- Supported communication standards and protocols (ISO, EPC)
- Regional (US, European and Asian) regulations
- Will the tag need to store more than just an ID number like an EPC?
- Anti-collision—how many tags in the field must be detected at the same time and how quickly?
- How fast will the tags move through the reader field?
- Reader support—which reader products are able to read the tag?
- Does the tag need to have security?
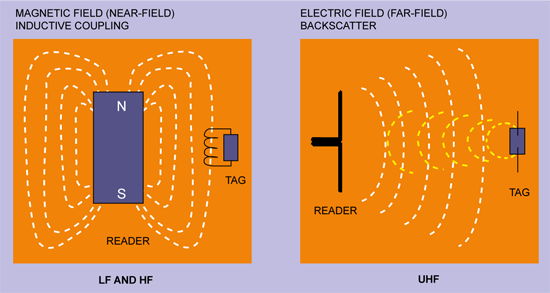
How tags communicate
In order to receive energy and communicate with a reader, passive tags use one of the two following methods shown in Fig. 6. These are near-field, which employs inductive coupling of the tag to the magnetic field circulating around the reader antenna (like a transformer), and far-field, which uses techniques similar to radar (backscatter reflection) by coupling with the electric field.
The near-field is generally used by RFID systems operating in the LF and HF bands, and the far field is used for longer-read-range UHF and microwave RFID systems. The theoretical boundary between the two fields depends on the frequency used, and is in fact directly proportional to l/2p, where ’l’ is wavelength. This gives, for example, around 3.5 metres for a HF system and 5 cm for UHF, both of which are further reduced when other factors are taken into account.

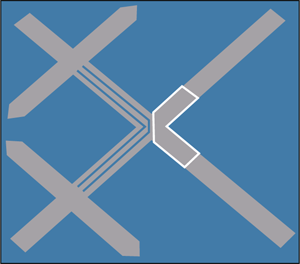
Tag orientation (polarisation)
How tags are placed with respect to the polarisation of the reader’s field can have a significant impact on the communication distance for both HF and UHF tags. This can result in a 50 per cent reduction of the operating range and, in the case of the tag being displaced by 90° (see Fig. 7), inability to read the tag.
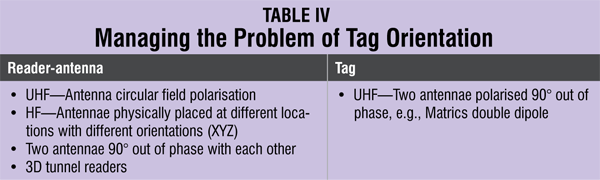
The optimal orientation of HF tags is when the two antenna coils (reader and tag) are parallel to each other as shown in Fig. 7. UHF tags are even more sensitive to polarisation due to the directional nature of the dipole fields. The problem of polarisation can be overcome to a large extent by different techniques implemented either at the reader or tag as shown in Table IV.
The future
Developments in RFID technology continue to yield larger memory capacities, wider reading ranges and faster processing. However, it is highly unlikely that the technology will ultimately replace barcode. Even with the inevitable reduction in raw materials coupled with economies of scale, the integrated circuit in an RF tag will never be as cost-effective as a barcode label. RFID, though, will continue to grow in its established niches where barcode or other optical technologies are ineffective, such as in the chemical container and livestock industries.










