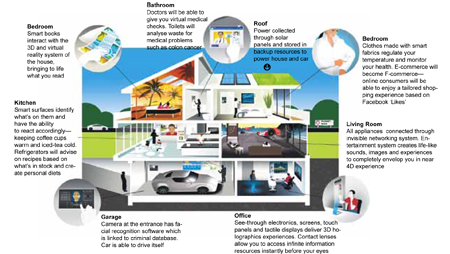
JUNE 2012: Those who have not heard of ubiquitous computing, or ubi-comp, often ask whether it is a new technology. Indeed, it is not merely a technology but a new paradigm of computing that Mark Weiser of Xerox PARC conceptualised about two-and-a-half decades ago. Prof. Ken Sakamura is also known to have proposed and demonstrated the concept in Japan through the TRON Smart House model in the 1980s.
Some rightly call ubiquitous computing the post-desktop paradigm of computing, while others call it the Internet of Things (IoT). In simple terms, ubi-comp represents a situation wherein technology is everywhere, but in an unobtrusive way.
In a ubi-com world, there will be innumerable computers embedded every-where, in everyday devices, from traffic signals and air-conditioners to coffee mugs and even clothes. There will be wearable centimetre-sized devices or tags, hand-held decimetre-sized devices and metre-sized interactive display devices. There will be micro-electro-mechanical systems from nanometre to millimetre scales and organic fabric-like devices. Dust-like devices will do some computing or communications without user interfaces. What is more, all these devices will have a unique ID or address and will connect through an intelligent network. The whole system will be so smart that an air-conditioner will be able to adjust the temperature based on the feedback from a sensor embedded in your dress.
This vision does not seem as incredible today as it seemed a decade ago, due to the technological developments that have happened in the recent past. For one, the number of connected devices in this world has grown a lot, and is likely to grow at a startling pace. Nanoscale devices are no longer a fantasy, we can now actually visualise or even see prototypes of ambient devices that are part of the décor. Connectivity has also improved a lot in the last few years, although how the traffic generated by a burgeoning ubi-comp environment will be borne by the backbone networks is still a question mark.
There has been major technological progress in many other aspects of ubi-comp as well: Unique ID schemes to identify the innumerable devices on the IoT, device- and system-level intelligence to make use of the information transacted by these devices, flexible displays, intuitive user interfaces and more. On the usage front too, there have been quite a few implementations of late, although these have been only at local or enterprise scales. Overall, we are moving steadily towards ubi-comp. But, as always, challenges remain.
A chip (or a code) in everything
Ubi-comp seems to require a chip in everything. Are current IC technologies capable of meeting this requirement in terms of functionality, volume and price-points?
“I think the current IC technologies suffice to meet the volume and price-points. Tags are getting cheaper,” says Chiaki Ishikawa, senior researcher and international liaison, YRP Ubiquitous Networking Laboratory, Tokyo, Japan. “Embedded computer chips have reasonable horsepower to do what they are asked to do most of the time. However, we may need to investigate more on the reduction of power consumption of these IC chips,” he adds.
The power needs of these ambient embedded devices are kind of special. These need to last almost forever without requiring replacement or losing power. Therefore in a ubi-comp future, it is likely that these embedded devices will mostly use renewable energy derived from ambient sources, such as light, heat or motion, with local energy storage capabilities to account for the intermittent nature of the energy source.
[stextbox id=”info”]There are many aspects that need to be looked into as we transition from the comparatively simple networks of today to a more complex ubi-comp world, network capacity being just one of them[/stextbox]
IC chips such as radio-frequency identification (RFID) tags are not the only means of implementing the IoT. There will also be many printed tags such as quick response (QR) codes. QR codes are basically square-shaped, black dots printed on a white background, wherein the printed pattern represents some information. We already see QR codes printed with advertisements these days—usually representing a URL. You can capture these codes on your mobile phone and directly go to the advertiser’s webpage. Ishikawa feels that the volume and usage of QR codes in ubi-comp will be much larger than IC-based ones.
Networking—technologies aplenty, challenges too!
Ubi-comp will require a networking architecture integrating technologies ranging from personal-area networking (PAN) right up to the wide-area communication networks. The PAN and LAN appear easier to manage, as we have a wide choice of interesting technologies at that level, including Wi-Fi, RFID, ZigBee, near-field communications (NFC) and Li-Fi.










