This article discusses the various high security design for remote controls.
Remote-controlled connected devices require security. Simple use cases include remote-operated door or bicycle locks (for smart bicycles used in bike sharing apps). This is usually done with the help of a secure element embedded in the platform. The secure element enables security functions that ensure strong resistance against malicious attacks and facilitate security life management of connected devices.
The secure element is basically a tiny chip that can perform cryptography and keep the secret keys safely hidden from attackers. Unlike microcontrollers (MCUs) and memories, it provides strong protection against attacks like differential power analysis and logical attacks.
Hardware-based security is an effective means of provisioning device keys, and protecting confidentiality and integrity of those keys. With hardware-based security, keys are programmed into security ICs in a secure environment, for example, during chip production or in a secure environment set up by the manufacturer. Once this is done, security ICs (with configured keys) are shipped to a manufacturer without having to disclose the keys.
Hardware-based security
A spokesperson from Qualcomm Technologies says, “A solid security approach uses a combination of integrated hardware-based security features. All features tightly integrated with the operating system, communication protocols, applications and the cloud help deliver new and exciting Internet of Things (IoT) products and services that also protect security and privacy. All defence technologies having these requirements must be hardwired down to the silicon to power IoT devices.
“At Qualcomm Technologies we have a portfolio of chips and software that spans everything from very high-end application processors to the simplest Bluetooth Low Energy (BLE) sensors. We design hardware and hardware-protected firmware to provide security features and superior robustness compared to software-only security solutions.”
Sambit Sengupta, associate director – field applications, Avnet India, says “The process of integrating a secure element in the industrial IoT ecosystem or device platform can become complex. The secure element can be used to provide security as a companion chip to most MCUs. We at Avnet help program the secure element securely and personalise it with unique IDs and secret keys. Multiple end users can benefit from this, where SIM cards, banking cards and so on are used.
“For commercial end applications, we find that brand protection and fake/spurious material authentication are required. We provide security solutions customised for such end uses. For example, one large water filter manufacturer wanted to protect its switched-mode power supply from fake brands. Such solutions were deployed to help him.”
Hwai Lin Khor, head of sales and business development – chipcard and security, Infineon Technologies Asia Pacific Pte Ltd, says, “Main components of a device include MCU, non-volatile memory (optionally embedded in MCU) and security IC that implements hardware-based security capabilities. Sensors and actuators complete the design. The key is to map the secure software update process to the device’s architecture.
“Infineon’s OPTIGA Trust X meets these security challenges faced by manufacturers. It is a turnkey, hardware-based solution offering enhanced security for connected devices, including secure firmware update functionality. It is easy to integrate and is TCG-compliant.”
Software-based security
For connected devices that can be controlled remotely, it is essential to have the ability to install new software. Software updates are used to add new features, fix bugs and resolve known security weaknesses. Highly automated software update processes that require little interaction and reduce downtime, however, represent possible entry points for attackers. If the connected devices are not properly protected, these may be left open to manipulation, typically through the installation of a malicious code on the devices, allowing the attacker to do what he or she wants it to do, which can include taking control of critical infrastructures, industrial automation systems or even cars.
With many of today’s connected devices, the user has to provide a password before the software image can be installed. The software itself may then have an additional layer of protection for integrity, for example, a cryptographic checksum (hash). The password protection scheme can be replaced or enhanced by cryptographic mechanisms, enabling authenticity and integrity checks, policy enforcement processing as well as optional confidentiality protection.
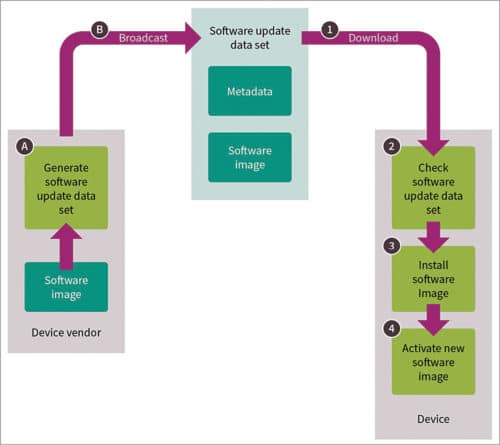
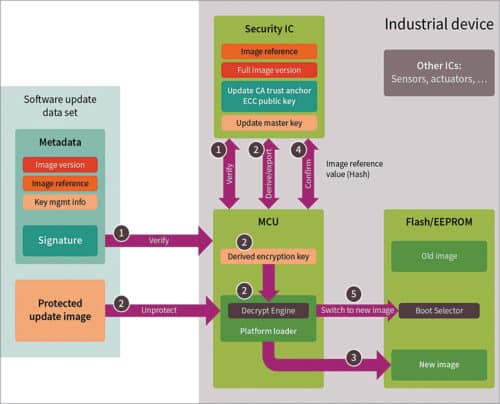
Software update is a set of data that contains the software code and information required for its proper installation. It contains the metadata describing software update image and conditions, the software update image itself and actual code that is loaded onto the device.
Metadata of a software update data set contains a wide range of data, including image version, image hash, image reference data and information on how the connected device should deal with the software update image.
Steps performed during a software update are:
- Secure storage of public key and secure verification of metadata signature
- Secure storage and handling of update master key for decrypting software image
- Copying software update image to target location
- Checking integrity of software image
- Activating new software image
Without further security measures, these data fields can be manipulated by an attacker. To equip the metadata with capabilities for securing the update process, followin cryptographic steps are required:
- Metadata itself must be integrity-protected. This is typically done via a cryptographic checksum called a hash value.
- Metadata should be electronically-signed, for example, with an elliptic curve signature that relies on a private key issued by the update root certification authority used by the device vendor.
- Signature should be verified using the corresponding public key stored securely on the device, ideally using hardware-based security storage features. If this verification fails, the update process is aborted.
Secure software update images can also be kept confidential. When these are transferred over public networks, confidentiality prevents reverse-engineering and protects against IP theft. To enable confidentiality, the device must know the decryption key. This can be done, for example, by deriving the update key from an update master key assigned to the device during manufacturing, and combining this with metadata. The key is derived by cryptographically combining a secret key with further device-specific information. This enables a higher security level than can be achieved by using the same secure software image decryption key over the device’s entire lifecycle.
Challenges of software-only security
Unfortunately, software has several inherent and significant weaknesses. It is written code that can be read and analysed. Once it has been analysed, it can be modified to the requirements of an attacker. Authentication process and system integrity can be broken, if a device is reprogrammed with modified software.
Inappropriate storage of secret keys during various processes and production steps is another potential weakness of software-based solutions. Attackers can easily identify secret keys in software-based protection systems, which are built into the software or otherwise stored in readable form.
Complete security design combines hardware with software
Software can be protected by hardware. Secure hardware detects faults and manipulation, and protects processing and storage of code using encryption, secure code and data storage. Software, thus, becomes trustworthy when combined with secure hardware.
There is one crucial difference between security and other features. With regular features, the update process only has to make sure that functionality has been correctly implemented. With security features, however, algorithms must be correctly implemented and secured against attacks. This is set to become an increasingly challenging task for many device manufacturers, as attack models are becoming more sophisticated.
Hardware-based security offers strong, tamper-proof protection for connected devices. Software, code and data are stored and processed in secure areas. Encrypted memory and processing, fault and manipulation detection as well as secure code and data storage combined enable a high level of protection.






