A radio-frequency identification (RFID) based access-control system allows only authorised people to enter a particular area of an establishment. Authorised people are provided with unique tags, using which they can access that area. This RFID based security system is based on micro controller AT89C52 and comprises a RFID module, a LCD module for displaying the status and a relay for opening the door. Fig.1 shows a user trying to open the door by placing an RFID tag near the RFID reader.
Radio-frequency identification
You might be familiar with RFID systems as seen in access control, contactless payment systems, product tracking and inventory control, etc. Basically, an RFID system consists of three components: an antenna or coil, a transceiver (with decoder) and a transponder (RF tag) electronically programmed with unique information.

Fig.2 shows a typical RFID system. In every RFID system, the transponder tags contain unique identifying information. This information can be as little as a single binary bit or a large array of bits representing such things as an identity code, personal medical information or literally any type of information that can be stored in digital binary format.
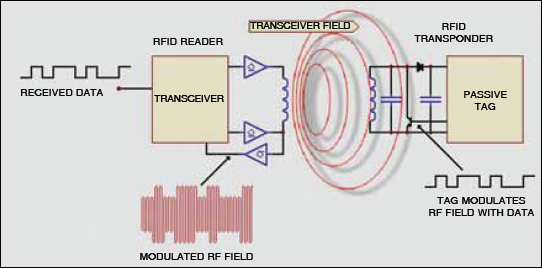
The RFID transceiver communicates with a passive tag. Passive tags have no power source of their own and instead derive power from the incident electromagnetic field. Commonly, at the heart of each tag is a microchip. When the tag enters the generated RF field, it is able to draw enough power from the field to access its internal memory and transmit its stored information. When the transponder tag draws power in this way, the resultant interaction of the RF fields causes the voltage at the transceiver antenna to drop in value. This effect is utilised by the tag to communicate its information to the reader. The tag is able to control the amount of power drawn from the field and by doing so it can modulate the voltage sensed at the transceiver according to the bit pattern it wishes to transmit.
Antenna
Fig.3 shows the internal diagram of a typical RFID antenna. An RFID antenna consists of a coil with one or more windings and a matching network. It radiates the electromagnetic waves generated by the reader to activate the tag and read/ write data from it.
Antennae are the conduits between the tag and the transceiver which control the system’s data acquisition and communication. These are available in a variety of shapes and sizes. Often, the antenna is packaged with the transceiver and decoder to become a reader, which can be configured either as a hand held or a fixed-mount device. The reader emits radio waves in ranges of anywhere from 2.54 cm (one inch) to 30 metres or more, depending upon its power output and the radio frequency used. When an RFID tag passes through the electromagnetic zone, it detects the reader’s activation signal. The reader decodes the data encode din the tag’s integrated circuit (silicon chip) and the data is passed to the host computer for processing.
Tags (transponders)
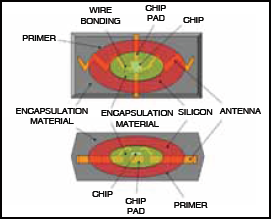
Fig.4 shows the internal structure of a typical RFID tag. An RFID tag comprises a microchip containing identifying information and an antenna that transmits this data wirelessly to the reader. At its most basic, the chip will contain a serialised identifier, or licence plate number, that uniquely identifies that item, similar to the way many bar codes are used today.

There are three types of tags: active, passive and semi-passive.
Passive tags have no internal power source. These draw their power from the electromagnetic field generated by the RFID reader and then the microchip can send back information on the same wave. The reading range is limited when using passive tags.
Active transponders have their own transmitters and power source, usually in the form of a small battery. These remain in a low-power ‘idle’ state until they detect the presence of the RF field being sent by the reader. When the tag leaves the area of the reader, it again powers down to its idle state to conserve its battery. As a result, active tags can be detected at a greater range than passive tags.
Semi-passive tags have their own power source that powers only the microchip. These have no transmitter. They rely on altering the RF field from the transceiver to transmit their data.
There are three ways for data encoding into tags:
1. Read-only tags contain data, which is pre-written onto them by the tag manufacturer or distributor.
2. Write-once tags enable a user to write data to the tag one time in production mor distribution processes.
3. Full read-write tags allow new data to be written to the tag as needed and later other data can be rewritten over the original data.
RF transceiver
The RF transceiver is the source of the RF energy used to activate and power the passive RFID tags. It may be enclosed in the same cabinet as the reader or it may be a separate piece of equipment. When provided as a separate piece of equipment, the transceiver is commonly referred to as an RF module. The RF transceiver controls and modulates the radio frequencies that the antenna transmits and receives. The transceiver filters and amplifies the back-scatter signal from a passive RFID tag.
RFID based security system circuit
Fig.5 shows the circuit of the RFID based security system. The compact circuitry is built around Atmel AT89C52 microcontroller. The AT89C52 is a low-power, high performance CMOS 8-bit microcomputer with 8 kB of Flash programmable and erasable read only memory (PEROM). It has 256 bytes of RAM, 32 input/output (I/O) lines, three 16-bit timers/ counters, a six-vector two-level interrupt architecture, a full-duplex serial port, an on-chip oscillator and clock circuitry. The system clock also plays a significant role in operation of the microcontroller.
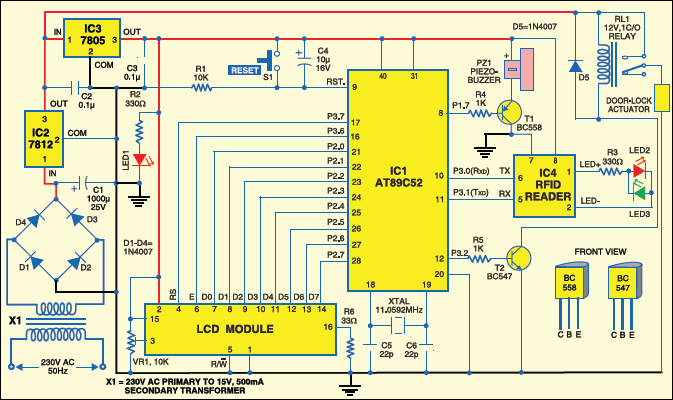

An 11.0592MHz quartz crystal connected to pins 18 and 19 provides basic clock to the microcontroller. Power-on reset is provided by the combination of electrolytic capacitor C4 and resistor R1. Switch S1 is used for manual reset. Port pins P2.0 through P2.7 of the microcontroller are connected to data port pins D0 through D7 of the LCD, respectively. Port pins P3.7 and P3.6 of the microcontroller are connected to register-select (RS) and enable (E) pins of the LCD, respectively. Read/write pin of the LCD is grounded to enable for write operation.
All the data is sent to the LCD in ASCII format for display. Only the commands are sent in hex form. Register-select (RS) signal is used to distinguish between data (RS=1) and command (RS=0). Preset VR1 is used to control the contrast of the LCD. Resistor R6 limits the current through the backlight of the LCD. Port pins P3.0 (RXD) and P3.1 (TXD) of the microcontroller are used to interface with the RFID reader.
Circuit operation
When an authorised person having the tag enters the RF field generated by the RFID reader, RF signal is generated by the RFID reader to transmit energy to the tag and retrieve data from the tag. Then the RFID reader communicates through RXD and TXD pins of the microcontroller for further processing.
Thus on identifying the authorised person, port pin P3.2 goes high, transistor T2 drives into saturation, and relay RL1 energises to open the door for the person. Simultaneously, the LCD shows “access granted” message and port pin P1.7 drives piezobuzzer PZ1 via transistor T1 for aural indication.
If the person is unauthorised, the LCD shows “access denied” and the door doesn’t open. LED2 and LED3show presence of the tag in the RFID reader’s electromagnetic field.
To derive the power supply, the 230V, 50Hz AC mains is stepped down by transformer X1 to deliver a secondary output of 15V, 500 mA. The transformer output is rectified by a full-wave rectifier comprising diodes D1 through D4, filtered by capacitor C1 and regulated by ICs 7812 (IC2) and 7805 (IC3). Capacitor C2 bypasses the ripples present in the regulated supply. LED1 acts as the power indicator and R2 limits the current through LED1.
A single-side PCB for RFID-based security system is given below for download. Assemble the circuit on a PCB as it minimises time and assembly errors. Carefully assemble the components and double-check for any overlooked error.
Software
The software for this project is given at the end of this article. It is written in ‘C’ language and compiled using Keil μVision4 compiler. The finally obtained ‘.hex’ code is burnt into the microcontroller using a suitable programmer. The program is easy to understand.
EFY note. The complete kit of this project is available with Kits’n’Spares. The source code of this project is available on the link given below.
Download PCB and component layout PDFs: click here
Download Source Code: click here







Sir,
We are recently working on the project named RFID based security system published at this site. We are having some problems as there is no specification of RFID module is given in the component list. Also we are having problem in programming of the microcontroller. Please tell me what number of RFID module is used in the circuit and also how we program the microcontroller. Please reply as soon as possible.
EM18 module