The first security camera system was installed by Siemens AG at Test Stand VII in Peenemünde, Germany in 1942, for observing the launch of V-2 rockets. The noted German engineer Walter Bruch was responsible for the design and installation of the system. It could be compared to a modern day closed-circuit television (CCTV) with regards to functionality. Today, all the applications one can think of using security cameras, involve some form of security related surveillance or the other.
However, like all aspects of technology, there are far more interesting use cases that can be implemented, using just a little ingenuity and some imagination. In this article, we are looking at the alternate applications for security cameras. You may find many of the applications one-off and extremely specific but they only go to prove that if you can widen your gaze, you can find solutions for anything, anywhere.
How Security Cams work
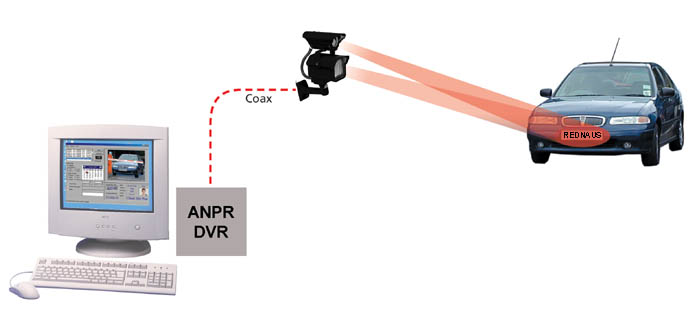
Unlike traditional television broadcasting, a CCTV sends a closed signal to the receiving monitor, allowing viewing to be strictly observed by the connected equipment. Surveillance cameras are capable of wide range viewing, so placing them in a corner area of the room will enable them to view a good portion of the room that is unobstructed. Picture quality has become quite impressive, with the monitors receiving video in high resolution, from the surveillance camera’s eye. Video Cassette Recorders (VCR’s) can also be connected to record the transmitted material on mass storage media for future reference.
Commonly, coaxial cable ties all of the relevant hardware together, but higher-end systems have incorporated wireless technology that eliminates the need to hide or bury wiring in walls, floors, and ceilings.
The resolution or the amount of detail that camera is able to capture depends on the specifications on the image sensor used. One important point to be kept in mind is that higher the quality of the image, more the space required for storage – so the engineer needs to find a balance wherein the CCTV provides enough clarity of image without sacrificing on storage space.
The ‘Other’ uses
Listed below are a few of the many alternate ways you can utilise a security cam. Security cams, now with the addition of readily available software, can be converted into an Internet Protocol (IP)/Network camera which extends the uses they can be put to. This allows applications such as remote monitoring and control, as well inteligent video analytics.
Remote Monitoring and Control
Live feed from selected cameras can be viewed from a device of our choice. It could be a laptop at some remote location, your smartphone or any such device. Commands can be transmitted for PTZ (Pan, Tilt, Zoom) cameras via a single network cable. Such modified IP cameras offer secure data transmission through encryption and authentication methods such as WEP, WPA, WPA2, TKIP, and AES. Modern IP cameras have the ability to operate without an additional power supply. They can work with the PoE (Power over the Ethernet) protocol which provides power to the cameras via the same ethernet-cable that transmits data.
Traffic Count on Highway
Feature points on vehicles are detected using proprietary software and tracked through the video sequence while specific algorithms remove the unnecessary features. Other algorithms are invoked to define a vehicle based on the feature points caught on camera. After that, for a section of the highway being monitored by a particular cam, the number of ‘vehicles’ crossing the path of the cam lens is counted. The novelty of the work includes an incremental, on-line, real-time algorithm to estimate the heights of features using a combination of background subtraction, perturbed plumb line projections, projective transformation, and a region-based grouping procedure. With a few changes in the algorithm, this technique can be adapted to counting not only vehicles but also people in a hallway.

Facial Recognition
There are various algorithms used to recognise a face. The two most common ones are:
1. Using Eigenfaces
2. Using Line edge map
Sonia Garg of Digitals India Security Products Pvt. Ltd explains, “In the eigenfaces technique, a collection of pictures of the individual is obtained and evaluated. Each image from the set contributes to a better definition of the individual’s face. With enough snaps, the system can identify the face perfectly. In the line edge method, the mouth, nose and eyes are taken as the most characteristic features. The faces are converted into grey level pictures which are then encoded into binary-edge maps”. This feature is not only resource-light but also is insensitive to illumination changes. The security cams are fitted with proprietary software having any one of the aforementioned algorithms to detect a human face. This is mostly used to screen for passengers on the no-fly list at airports and at other security critical areas. It has also been used to identify voter fraud and for identity proof purposes amongst other uses.




