Historically, it has been a challenge to visualise fingerprints on thermal paper, Fear redefines security in every era. Huts began to have doors when people began to worry about their privacy; and forts began to have moats when kings started invading. Banks began to have passwords, homes began to have locks, phones and computers began to have pass-codes, and slowly security became a basic amenity, an all-pervading necessity. As in any field, technology rose to the occasion, and from homes to national borders, high tech began to be deployed at every turn. Still, security and privacy continue to be serious concerns for everybody, albeit of varying degrees.
As always, technologists continue their quest for newer technologies that can protect places, people, and now, their devices and data too. Here, we look at a small sample of the security-related research and experimentation happening across the world. To show how vast an area it is, we shall look at disparate examples that span from data security to public security.
Using the cloud without compromising privacy
In most instances, there is a paradox in using cloud-based services and strong encryption schemes. When you need to perform some operation, say search, on a strongly encrypted database stored on the cloud, but the server cannot decrypt the data, it has no choice but to return all the records to you, letting your computer assume the burden of decrypting and searching the database. So, although your data is secure, the whole point of offloading work to a cloud server is lost in the bargain! On the other hand, if you let the server decrypt the message by sharing the key, security and privacy are compromised.
IBM came out with a solution to this problem, and was granted a patent on it in December 2013. Their ‘fully homomorphic encryption’ offers a way for servers (including cloud ones) to take encrypted data from a user, process it, and send back an encrypted result–all without decrypting the data first! In short, they have solved a mathematical puzzle that has daunted scientists for years–that is, querying of encrypted data without decryption. The first results related to homomorphic encryption were revealed by IBM researcher Craig Gentry in 2009. Although a significant breakthrough, the technique was complex and would take too much time.
As one particular critic pointed out at that time, “Performing a Google search with encrypted keywords—a perfectly reasonably simple application of this algorithm—would increase the amount of computing time by about a trillion.” However, the technique gained new hope in 2013, when two more IBM researchers, Victor Shoup and Shai Halevi, took up Gentry’s original concept and implemented it more practically. They released an open source, GPL-licensed C++ library to perform homomorphic encryption at a low level. They are working on providing higher-level routines.
Other researchers from reputed institutes like the University of Toronto and Massachusetts Institute of Technology are also working on similar techniques, but are all faced with the challenge of making these algorithms faster and more computationally practical.
Non-invasive parcel scanner
How cumbersome it is when the post office or courier insists that you seal the packet in their presence after they check it for explosives and drugs? The T-Cognition system is a terahertz scanner developed by researchers at the Fraunhofer Institute for Physical Measurement Techniques IPM in Kaiserslautern in collaboration with Hübner GmbH & Co. KG in Kassel, which helps scan the content of packages or envelopes without having to open them. In specific, the system helps recognise parcels containing hazardous, flammable materials such as explosives and illicit drugs.
The scientists chose to use waves in the terahertz range for scanning, because this lies midway between microwave and infrared in the electromagnetic spectrum, and thus combines the advantages of both. These low-energy frequency waves can easily penetrate paper, wood, lightweight fabrics, plastics and ceramics. The characteristic spectra generated by them can be analysed using intelligent software to accurately detect the type of material they travel through. Also, since terahertz waves are non-ionising, they are safe to use without any special shields.
Although very useful for mail scanning, this nascent technology can also be used for other security applications such as industrial security, airport security, and so on.
New light for scouting fingerprints
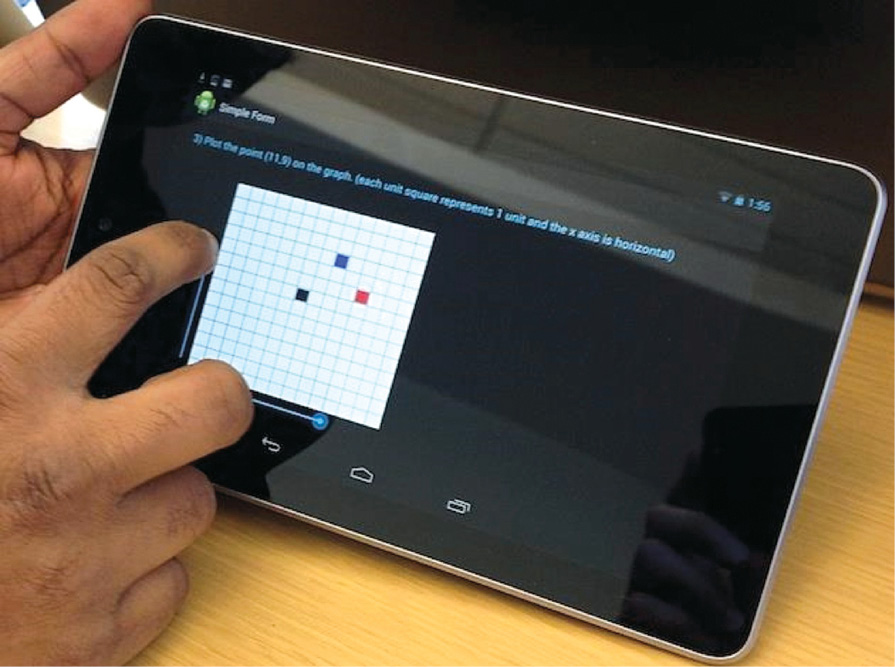
When we say tech in security, it is not just about high-tech video surveillance and cloud-based analysis. Sometimes, simple breakthroughs can be big, such as this new UV light developed at the University of Leicester to identify fingerprints on thermal paper used for printing receipts, ATM bills, etc—a key requirement for solving several financial crimes.