Read Part 1
A wireless sensor network is a communication system which senses and gathers information from a certain area and sends it to where it is required. In such networks the communication system requires networking protocols which are efficient, reliable, scalable and secure.
Fundamental differences in sensor networks which affect protocols are:
Data sink(s). That is, the nature of data sink(s). For example, whether the end user is embedded in sensor network or access points
Sensor mobility. This aspect may influence protocols at the networking level as well as at localisation service
Sensor resources. Such as computing ability
Traffic pattern. For example, whether data is generated continuously during environmental monitoring
The factors to be considered while designing WSN protocols are:
1. Routing decisions to be undertaken considering the importance of energy resources in the network.
2. Communication channels often exist between events and sinks. Since sink nodes are typically used for overall description of the environment rather than explicit readings from the individual sensor devices, the communication in sensor networks is normally referred to as data-centric rather than address-centric, and the data may be aggregated locally rather than collecting all the raw data sent to the sink(s).
3. Sensors have the knowledge of their own location to usefully assess their data. The location information can be utilised for routing purposes.
4. If a sensor network is well connected, the topology control service should be used in conjunction with the normal routing protocols.
Multiple access protocols
When multiple nodes desire to transmit, protocols are needed to avoid collisions and loss of data. In frequency division multiple access (FDMA), different nodes have different carrier frequencies. FDMA also requires additional hardware and intelligence at each node. In code division multiple access (CDMA), a unique code is used by each node to encode its messages. However, this increases complexity of the transmitter and receiver.
In time division multiple access (TDMA), the RF link is divided on time axis with each node given a predetermined time slot it can use for communication. This decreases the sweep rate, but a major advantage is that it can be implemented in software. All nodes require accurate, synchronised clocks for TDMA.
Medium access control protocols
Medium access control (MAC) protocols focus on reducing the idle power consumption by setting the sensing transmitters to sleeping mode as often as possible. MAC protocols have been designed for ad-hoc networks which primarily focus on optimising fairness and throughput efficiency with less emphasis on energy conservation. Some protocols like IEEE 802.11 eliminate the waste caused by colliding packets in WSNs. Some others avoid unnecessary reception of packets by nodes that are unintended destinations. It has been assessed that idle power consumption can be of the same order as that consumed by the transmitter and receiver. Some of the MAC protocols are described below.
S-MAC. This protocol creates a sleep schedule that determines when to activate the receivers and when to put them in sleep mode.
Timeout-MAC (T-MAC). It eliminates idle energy further; instead of allowing the messages to be sent continuously, messages are transmitted in bursts in the beginning of the frame.
DMAC. Since many WSNs have data-gathering trees routed to a single data sink in the direction of packets arriving at a node, DMAC takes advantage of this by staggering the wakeup times for nodes based on their distance from the data sink.
Traffic-adaptive medium access (TRAMA). Aforementioned protocols help in minimising the power consumption by reducing the time that the transmitters remain in idle state, TRAMA attempts to reduce wasted energy consumption caused by packet collisions. Nodes determine their transmitting state using adaptive election algorithm (AEA). In AEA, each node calculates a priority for itself and all two-hop neighbours for the current slot. If a node has the highest priority for that slot and has data to send, it wins that slot and sends the data. If one of its neighbours has the highest priority, it sets itself to the receiving mode. In short, AEP assigns priorities for the unused slots to the nodes needing extra slots.
Sparse topology and energy management (STEM). When data packets are generated, the sensor generating the traffic uses a paging channel (separate from the data channel) to awaken the downstream neighbours.
Storage technology for portable devices
Flash memory has been the most reliable storage technology. However, visible limitations for future Flash cell scaling include power consumption, charge storage requirements of the dielectrics, reliability issues and capacitive coupling between adjacent cells. Efforts are being made to reduce these limitations through system management techniques and fabrication technology (such as high k-dielectrics, nano crystal storage media and Fin-FET). However, there is no doubt that Flash will remain the dominant non-volatile memory technology at least down to 45nm node. Nevertheless, there are new memory technologies available, such as ferro-electric RAM (FeRAM), magnetic RAM (MRAM), ferro-electric polymer RAM (FePRAM), phase change memory (PCM), resistive RAM (RRAM), probe storage, carbon nano-tube memory (CNT) and molecular memory. The most promising are probe storage memories and PCM.
IEEE 802.16
IEEE 802.16 working group has come up with a standard called broadband wireless access (BWA), commonly known as WiMAX (worldwide interoperability for microwave access). IEEE 802 .16 has specified two aspects of the interface for WiMAX, the physical layer (PHY) and the media access control layer (MAC).
The physical layer defines electrical and physical specifications for a device’s establishment and termination of connection to communication medium, communication flow control, modulation coding, etc. It was designed to accommodate the need for a low cost yet allowing for high levels of integration. The use of direct sequence allows the analogue circuitry to be very simple and very tolerant towards inexpensive implementations.
The MAC layer was designed to allow multiple topologies without complexity. The power management operation does not require multiple modes of operation. The MAC allows reduced functionality device (RFD) that need not have Flash or large amounts of ROM or RAM.
MAC is divided into three sub-layers: convergence, common part and security (or privacy). The convergence sub-layer describes how wireline technologies, such as asynchronous transfer mode (ATM), Ethernet 802.1 (LAN/MAN) and Internet protocol (IP) are encapsulated on the air interface and how data is classified.
The common part sub-layer is responsible for idle-mode processes like cell selection, paging structures and location-area updates. This layer is also responsible for sleep-mode processes, handover procedures, multicast and broadcast services, quality-of-services class and automatic repeat request (ARQ) processes. It also does header suppression, packing and fragmentation for efficient use of spectrum.
The security sub-layer provides the subscribers with privacy, authentication or confidentiality across the broadband wireless network. It uses encapsulation protocol and privacy key management (PKM) protocol. One of the features of MAC layer of 802.16 is that it is designed to differentiate service among traffic categories with different multimedia.
WiMAX is a wireless metropolitan area network technology which fits between wireless local area networks and wireless wide area networks. This standard introduces many advantages including variable and high data rate (up to 75Mbps), last-mile wireless access (up to 50kM), point-to-multipoint communication, large frequency range and quality of service.
WiMAX supports two network architectures, namely, point-to-multipoint (PMP) mode and mesh mode. PMP network has one base station (BS) and multiple subscriber stations (SSs) The BS is the central control point and regulates all the traffic on the network. The multiple access schemes in WiMAX include both frequency division duplexing (FDD) and time division duplexing (TDD). TDD is more flexible than FDD.
The performance of IEEE 802.16 is assessed by throughput and delay. Throughput of scheduler is defined as the maximum bandwidth allocated by the scheduler with respect to the requested data rate by the subscriber stations, and the delay is defined as the time taken by the scheduler to allocate bandwidth for the packet in queue.
IEEE 802.15.4 defines a total of three frequency bands of operation: 2.4GHz, 915MHz and 868MHz. The 2.4GHz band offers a total of 16 channels (channel 11-26), 915MHz offers 10 channels (channel 1-10), and 868MHz offers just one channel (channel 0). The bit rate of the protocol depends on the selection of frequency of operation.
| Frequency | Bit rate | Channels – Range |
| 2.4GHz | 250kbps | 16 (11-26) |
| 915MHz | 40kbps | 10 (1-10) |
| 868MHz | 20kbps | 1 (0) |
The maximum length of an IEEE 802.15.4 MAC packet is 127 bytes. Each packet consists of header bytes and 16-bit cyclic redundancy check (CRC) value. The 16-bit CRC value verifies the frame integrity. In addition, it optionally uses an acknowledged data transfer mechanism. With this method, all frames with a special ACK flag set are acknowledged by its receiver.
IEEE 802.15.4 based WSNs can support a maximum of 250kbps for 2.4GHz bandwidth. Therefore WSNs are employed in areas requiring intrusion detection or fire alarm, and where the packets are generated at very low data rates.
Network topology
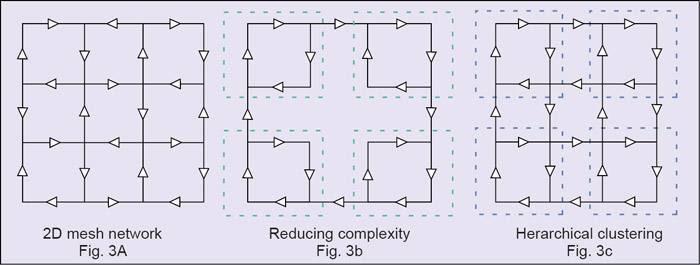
The basic issue in communication networks is the transmission of message to achieve a prescribed message throughput quality of service (QoS) and quantity of service. Depending on QoS, installation in the environment, economic considerations and the application, one or a combination of the following topologies may be adopted: fully connected, mesh, star, ring, tree or bus. Of these, mesh type with some modifications has been found to be more useful (see Fig. 3(a)).
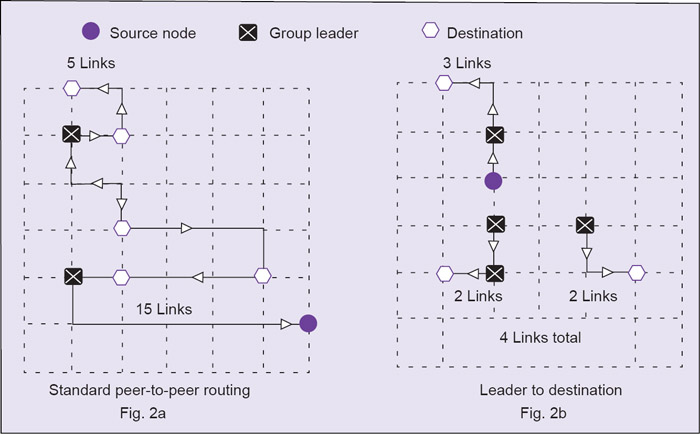
Mesh networks are regularly distributed networks that generally allow transmission only to a node’s nearest neighbours. The nodes in these networks are generally identical, so the mesh networks are also referred to as peer-to-peer (see Fig. 2(a)). Mesh networks are good for large WSNs that are distributed over a geographic region, such as personnel or vehicle security surveillance systems. Another advantage of mesh networks is that, although all nodes are identical and have the same computing and transmission capabilities, certain nodes can be designed as ‘group leaders’ that take on additional functions (see Fig. 2(b)).
Multicast systems in mesh networks use a hierarchical leader based scheme for message transmission. Each group of nodes has a designated leader that is responsible for receiving messages from and transmitting to nodes outside the group. The group leader for communication should be the entry node of each group, while the group leader for DSP should be the exit node. Multicast routing improves efficiency and reduces message path length (see Fig. 2).
Routing tables for distributed networks increase exponentially as nodes are added, and hence the number of links increases exponentially. To simplify the network structure, one can use hierarchical clustering techniques (see Fig. 3(c)). The hierarchical structure must have the same structure at each level.
Hierarchical network structure simplifies routing and is also amenable to distributed signal processing and decision making, since some processing can be done at each hierarchical layer. Failure recovery is also straight-forward. If a link fails, one may simply switch in one of the disabled links to take over. Hierarchical structure must be consistent, that is, it must have the same structure at each level.
Edge binding. The phenomenon of edge binding means that much of the routing power of peripheral stations is wasted because peripheral links are unused. Thus message tends to reflect the boundary into the interior or move parallel to periphery. To avoid this, the Manhattan geometry connects the nodes at one edge of the network to nodes at the opposite edge, thereby reducing the complexity (see Fig. 3(c)).
Power management. With the advent of ad hoc networks of geographically distributed sensors in remote site locations, there is a focus on increasing life time of sensor nodes through power generation and power conservation. Researchers are designing micro-electro-mechanical systems (MEMS), which can generate power using solar, vibration and thermal energies.
Miniature RF components for transceivers. RF identification (RFID) devices can also be used for power management purposes. The transponder micro-circuit has an L-C tank circuit which stores power from received interrogation signals, and uses that power to transmit a response. RFID operates in a low frequency range of 100kHz to 1.5MHz, or a high frequency range of 900MHz to 2.4GHz, and has an operating range up to 30 metres. TDMA is especially useful for power conservation, since a node can remain inoperative between its assigned time slots and wake up in time to receive and transmit messages.
The required transmission power increases as the square of the distance between source and destination. Therefore multiple short message transmission hops require less power than one long hop. A current topic of research in power controls is that each node cooperates with all other nodes in selecting the individual transmission power level.
Smart sensors
The IEEE 1451 standard makes it easier for different manufacturers to develop smart sensors and to interface these devices to networks. A smart sensor is a sensor that provides extra functions beyond those necessary for generating a correct representation of the sensed quantity. These include signal conditioning, signal processing and decision making/alarm functions.
Main objectives of smart sensors are: (a) move the intelligence closer to the place of measurement, making it cost-effective to integrate and maintain distributed sensor systems, (b) clustering of transducers, (c) control, compute and communicate for a common cause and (d) seamlessly interface many sensors of different types. The concept of virtual sensor is also fulfilled.
A virtual sensor, a component of smart sensor, is a sensor/transducer plus the associated signal conditioning and DSP. MEMS sensors are now well developed and are available for most sensing applications in WSNs.
Transduction mechanisms of sensors
Traducers convert energy from one domain to another and their outputs are generally voltages or currents. The sensory transduction may be carried out by using any one or more of the following effects of physical principles: piezo-resistive, piezo-electric, capacitive, inductive, magnetic or electro-magnetic, magneto-resistive, magnetic field, thermal (thermo-mechanical, thermo-resistive, thermocouples, resonant temperature sensors, thermopiles or bolo meters).
Optical transducers. These make use of photo-electric effect, photo-conductive effect, or optical-fibre based technology (for instance, devices like accelerometers often use time-of flight information, IR detectors or UV detectors).
Electro-chemical, chemical and biological. Used for solids, liquids and gases, these include metal-oxide gas sensors, interdigitated-gate electrode FETs (IGFETs) and their arrays, ion-sensitive FETs (ISFETs) like ionophone, quartz crystal micro-balance (QCM) and micro-cantilevers. Types of gases that can be monitored using metal-oxide gas sensors are CO2, CO, H2S and Nh3. Other applications are in medical diagnosis of smallpox, anthrax chemical warfare, food monitoring, security and surveillance (using implantable bio-sensors).
Acoustic wave sensors. Such sensors as surface acoustic wave (SAW), thickness shear mode (TSM) and flexural plate wave (FPW) make property changes, such as mass into detectable electrical signals.
Commercially available nodes come with five sensors installed for temperature, light, acoustic, acceleration/seismic and magnetic effects. Especially suitable for surveillance purposes, these work with operating frequency of 916MHz or 433MHz, with a data rate of 40k bits/sec, having a range of 10 to 30 metres. Installation of these devices requires a great deal of programming.
Ultra wide band (UWB) is of great interest in distributed networks, since UWB is a short-range technology that can penetrate walls. It is suitable for multi-node transmissions and has built-in time-of-flight properties that make it very easy to measure ranges down to 1cm with a range of 40m.
Moreover, UWB transceivers can be made very small and are amenable for MEMS technology. Since in pulse position modulation no carrier is needed, it means the antennae are not inductive. But signals coming from MEMS may be very noisy, of low amplitude, biased and dependent on secondary parameters, such as temperature, which is an undesired characteristic. That is why the signal conditioning circuits are very essential.
The author is director (R&D) at Global Institute of technology, Jaipur






