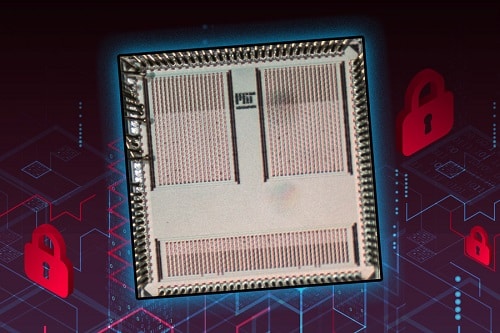
The small sized, low energy consuming chip is equipped with advanced encryption techniques to prevent information leakage from a smart device
In this age of increased digitalisation where several electronic devices seem to be connected to the internet for faster processing and storage of critical data, the chances of cyberattacks on them through a side-channel attack for malicious purposes is a grave concern. A side-channel attack seeks to gather secret information by indirectly exploiting a system or its hardware. A savvy hacker could monitor fluctuations in the device’s power consumption while the neural network is operating to extract protected information that “leaks” out of the device. Existing methods to prevent side-channel attacks consume a lot of power, making them unfeasible for low-powered IoT devices like smartwatches.
Now the research team from the Department of Electrical Engineering and Computer Science (EECS) at MIT has devised a small-sized integrated circuit chip that can protect against high-powered side-channel attacks while using much less energy. The chip is beneficial for incorporation into smartwatches, smartphones or tablets to perform secure machine learning computations on sensor values.
“The goal was to build an integrated circuit that did machine learning on the edge, so that (even though being low-powered), it protected against side-channel attacks and ensured privacy,” said Anantha Chandrakasan, Vannevar Bush Professor of Electrical Engineering. “People have not paid much attention to the security of these machine-learning algorithms, and this proposed hardware is effectively addressing this space.”
Based on threshold computing, the chip has a neural network that splits data into unique, random components and operates upon them, in a random order, before accumulating the final result. Using this method, the information leakage from the device is random every time, thereby not revealing any actual side-channel information.
But this approach is more computationally expensive since the neural network runs more operations, and also requires more memory to store the jumbled information. On top of that, although existing secure computation methods like homomorphic encryption guarantee strong security, they incur huge overheads in area and power, limiting their use in many applications.
So, to optimise that and slash the required computing power, a function was used that reduced the multiplication of the neural network needed to process data. For more security, while reducing the amount of memory needed on the chip, the neural network model was encrypted with various parameters. Streamlining the silicon chip architecture reduced the space required compared to similar security hardware.
“By using this special function, we can perform this operation while skipping some steps with lesser impacts, which allows us to reduce the overhead. We can reduce the cost, but it comes with other costs in terms of neural network accuracy. So, we have to make a judicious choice of the algorithm and architectures that we choose,” said Saurav Maji, a graduate student in MIT’s Department of Electrical Engineering and Computer Science (EECS).
While providing security against power side-channel attacks, the chip requires 5.5 times more power and 1.6 times more silicon area than a baseline insecure implementation.
“We’re at the point where security matters. We have to be willing to trade off some amount of energy consumption to make a more secure computation. Future research could focus on how to reduce the amount of overhead to make this computation more secure,” said Anantha Chandrakasan.
After all such enhancements, the chip performed commendably in a real-world implementation with different data signal types compared to a chip that had no security hardware.
“Security adds a new dimension to the design of IoT nodes, on top of designing for performance, power and energy consumption. This ASIC or Application-Specific Integrated Circuit nicely demonstrates that designing for security, in this case by adding a masking scheme, does not need to be seen as an expensive add-on,” says Ingrid Verbauwhede, professor in the computer security and industrial cryptography research group of the electrical engineering department at the Catholic University of Leuven, who was not involved with this research. “By selecting masking friendly computational units, integrating security during design, even including the randomness generator, a secure neural network accelerator is feasible in the context of an IoT,” she adds.
In the future, the researchers hope to apply this approach to electromagnetic side-channel attacks, which is harder to defend, since no physical device is needed to collect hidden information.