In today’s world, where technology is deeply ingrained in our daily lives, system security has become an increasingly crucial aspect of our digital existence. cyber security is the practice of protecting computer systems and networks from unauthorized access, theft, damage, or misuse. Let us try to understand these threats and see how we can deal with them.
Today, we are living in a world with more than 20 billion connected devices. We call these devices smart because they can do smart jobs. They know what to do; they are intelligent enough to find their own algorithms to work on. On top of that they are able to run smart programs.
Unfortunately, these programs are not always as smart as we think them to be. They often contain bugs. We have various security models to counter these bugs and we know how to secure our systems in this industry, but even then we continue to face new challenges with security.
So, the question is, what went wrong with the Internet of Things (IoT) devices, and why the security that we have today is not enough? The three problems that could explain this are connectivity, extensibility, and complexity.
Connectivity: Today, there are over 20 billion connected devices available, which is about times the population of the world. If one of these devices is compromised, there is a good chance of the rest of the connected devices get compromised as well. The scary part is that most of the important nodes of critical infrastructure are connected to the same internet.
Extensibility: We are using the same code over and over again. For example, various Linux kernels use the same code to function. Then there are Android devices for which no new code is being written. One of the major drawbacks of reusing the same code over and over again is that the persisting security flaws get propagated along the way.
Complexity: Computer programs get complex over time. Windows 10, for instance, has over 50 million lines of code. Google offers two billion lines of code. More lines of code directly equate to more bugs and flaws. These bugs act as a gateway for attackers and hackers.
How to Protect Against Cyber Attacks?
Hackers have a plethora of tools in their arsenal. They find out the flaws in a system using these tools and then exploit them.
Shodan is one of the tools that can let you know whether your system is compromised or not. It is a search engine similar to Google, but it crawls down to all the devices connected to the internet and then creates a database of those devices.
You can just put any internet protocol (IP) address in the search, and Shodan will present you with all the information about it along with the problems associated with it. On top of this, with the help of some keywords, you can find out the connected cameras and information about their owners, and configurations of the traffic signals.
Also Read: Fake Apps Possess a Threat to Cyber Security
Challenges Explored So Far…
In the last three decades, we have had so many cyber security models derived for information security. We have learned that confidentiality, availability, and integrity (CIA triad) is what needs to be protected at all cost.
In today’s world security falls short when it comes to cybersecurity systems or smart systems. About ten years ago a malware known as Stuxnet shook the entire world. It was the first time we discovered that a computer worm is not messing up only with our data.
This particular worm was able to compromise the programmable logic controller (PLC) board of a nuclear reactor. One-fifth of all the nuclear reactors in Iran, along with many others in various other countries, were reported to be compromised by this worm. Eighty percent of the power companies in Mexico were affected. Sixty percent of the power companies in India were also the victim of this worm.
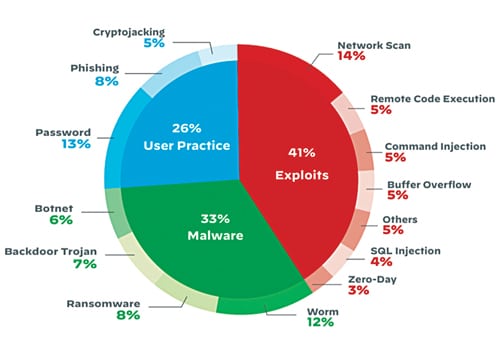
It was these moments that made us realize that we should not only be just protecting our data but our lives could also be dependent on it. Smart security does not just mean information security, and that’s why we have to rebuild and retrain all of the models that we have today. We are still not quite there yet.
What Could Go Wrong?
It is entirely possible that there are issues (some misconfigurations, poor codes, etc.) with our web server, the web app, the mobile app, application programming interface (APIs), or there may be problems with the Google Cloud, routers, etc.
Today, we have automated cars that offer a wide range of functionality through an app that could be installed on your smartphone, but it is not secure enough. Then there are smart cameras, smart buildings, warfare equipment, medical devices, smart cities, airplanes on auto-pilot, and much more that could be compromised with the lack of IoT security.
Following are some of the major reasons, as identified by OWASP, for the occurrence of such IoT security flaws:
- Weak, guessable, or hardcoded passwords
- Insecure network services
- Insecure ecosystem interfaces
- Lack of secure update mechanism
- Use of insecure or outdated components
- Insufficient privacy protection
- Insecure data transfer and storage
- Lack of device management
- Insecure default settings
- Lack of physical hardening
An important thing to note here is that we have a huge attack plane that none of the hardware or the software can detect. In order to defend our systems from hackers or attackers, there are only two important things that we can do as defenders—monitoring and testing. There are certain types of attacks that can be avoided easily by performing code reviews, statistical analysis, training the developers, etc.
Even though there are many solutions readily available, they are not quite feasible. For mid-range mobile phones, due to tough market competition, a manufacturer cannot spend more than three months to implement and market a new feature in their product. If they take a longer time for security testing and bug fixing, their competitor company might do it sooner and market it.
Penetration testing also presents itself with a very high cost. It can cost anywhere from $4,000 to $10,000 per product version to a company, which can be too much for them if they want to keep a competitive price advantage.
Cyber security is not the sole responsibility of one person or entity. Rather, it is a collective effort that requires the participation of everyone involved in the process.
Individuals, whether they are employees or customers, must be aware of their role in maintaining system security. They need to take responsibility for their actions, such as creating strong passwords, not sharing their login credentials, and reporting suspicious activities.
Ultimately, everyone must make a conscious effort to prioritize security and take action to maintain it. By working together and taking collective responsibility, we can all play a role in keeping our systems secure.
This article is based on a tech talk by Dr Soumyo Maity, Senior Principal Engineer, Dell Technologies at India Electronics Week 2022. It has been transcribed and curated by Laveesh Kocher, a tech enthusiast at EFY, who has a knack for open-source exploration and research
Dr. Soumyo Maity is Senior Principal Engineer at Dell Technologies





