- Panasonic Corporation’s new launch has a unique authentication feature that is similar to an OTP or a human fingerprint
- The IC has capability for short-range wireless communication and is highly resistant to radiation
 With an increase in IoT devices across various fields, data attacks have consequently become rampant. In order to protect these devices, an authentication key is conventionally written in an IC memory. While this is an efficient way of securing data against any unauthorized breaches, attackers nowadays have become quite advanced and are using sophisticated malicious techniques to retrieve information.
With an increase in IoT devices across various fields, data attacks have consequently become rampant. In order to protect these devices, an authentication key is conventionally written in an IC memory. While this is an efficient way of securing data against any unauthorized breaches, attackers nowadays have become quite advanced and are using sophisticated malicious techniques to retrieve information.
Now, Panasonic Corporation has developed a multifunctional, secure IC for equipping electronics designers to provide enhanced security measures for several IoT, IIoT and medical devices.
Chip Specifications
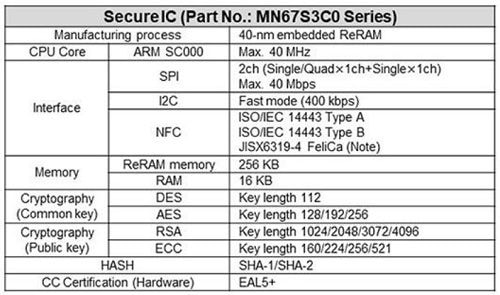
Wireless Communication
The IC comes with NFC (Near Field Communication) for short-range wireless communication and ReRAM (Resistive Random Access Memory) that is highly resistant to radiation.
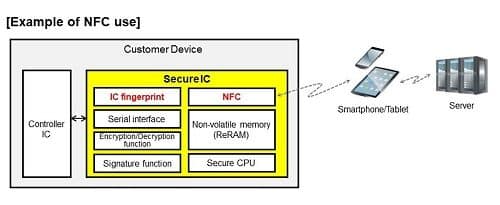
NFC enables devices that are not connected to the internet to get an internet connection via smartphones and tablets. The use of energy harvesting technology (for obtaining electric power by using sunlight, machine-generated vibrations and heat, and electromagnetic waves) allows smartphones and tablets to read controller IC information and device incident records for configuring secure device operation settings – even when the device power is off.
ReRAM’s high resistance to radiation makes it suitable for safe sterilization of medical equipment and pharmaceuticals using radiation.
Tamper-Proof Authentication
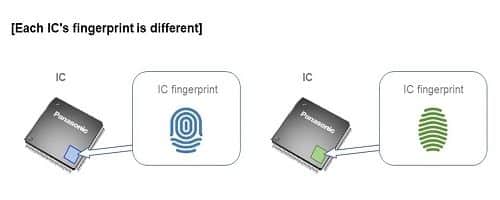
A unique characteristic of Panasonic’s new product is that the IC-specific analogue information (i.e. IC fingerprint) is different for each IC (just as each human has a different fingerprint). Therefore, no IC fingerprint can be copied and used in place of another.
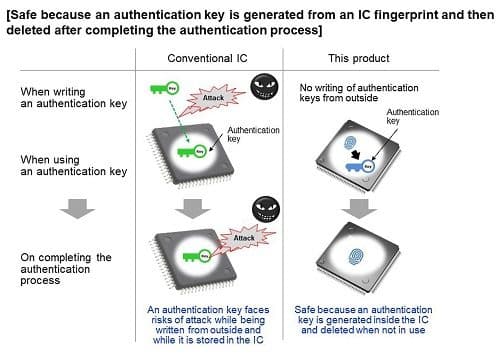
As an added measure to prevent any tampering, the generated authentication key gets automatically deleted after its use, thereby boosting the security feature of the IC and effectively protecting important data.
IoT Security Compliant
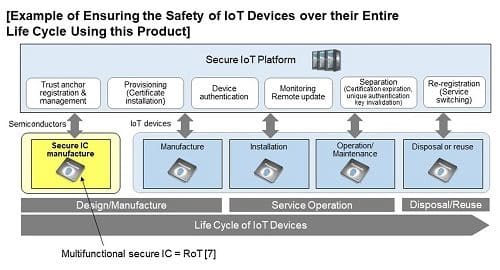
A certificate-based authentication ensures that the safety of the device stays intact during its entire life cycle – from manufacture to disposal/reuse. This facilitates compliance with the security standards that govern IoT systems.
The company has begun shipping samples since February 2020






