With so many government, commercial, defence and private systems connected to the ubiquitous Internet, cyber threats are becoming a major concern. It is important for everyone to know about various types of cyber threats in order to safeguard the confidentiality, integrity, authenticity, reliability and availability of data transmitted over the interconnected networks. Here is an overview
Dr Rajiv Kumar Singh
The use of information technology (IT) has changed our lives dramatically. Nearly all our basic societal activities and daily routines like financial transactions, ticketing, hotel booking, communication with others and working of any organisation depend on the functionality of the digitally operated and interconnected computer world.
This digital world, with or without the use of interconnected networks, is threatened by cyber criminals who try to steal important data about the user (such as credit card numbers, bank account information, user ID and password). Besides, they can damage information on the user’s computer, install unwanted software without the user’s consent, allow someone else to control the user’s computer remotely, use the user’s computer resources (such as hard disk space, fast processor and Internet connection) to attack other computers on the Internet), etc. In some cases, intruders take advantage of a particular vulnerability in one of the programs installed in the computer to gain access.
Given these risks, it is very important for everyone to have knowledge about cyber threats in order to safeguard the confidentiality, integrity, authenticity, reliability and availability of data transmitted over interconnected networks.
Cyber threats
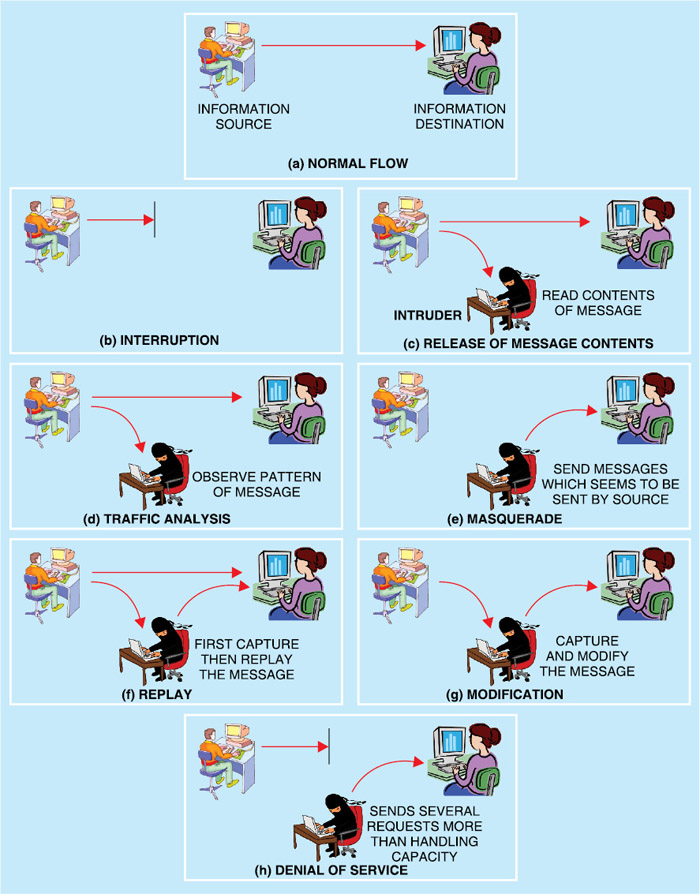
Cyber threats are usually classified as passive and active attacks. Passive attacks try to eavesdrop to learn contents or make use of information from the system without affecting the contents and system resources. In this way, passive attacks may be used for release of message contents and traffic analysis (observe pattern of messages, traffic flows, etc).
Active attacks, on the other hand, attempt to alter system resource, or affect their operation, in addition to modification of content and/or participation in communication in order to impersonate legitimate users (masquerade), replay, retransmit or modify the content in transit, and launch denial-of-service (DoS) attacks (Fig. 1).
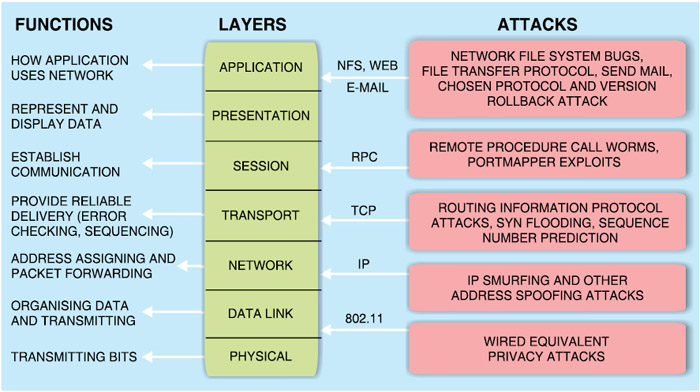
Every computer on a network operates on the seven-layer architecture of Open System Interconnection (OSI) model developed by International Telecommunication Union (ITU). Specific functions of each layer and possible cyber attacks are shown in Fig. 2. It is noteworthy here that the entire security system is only as secure as the single weakest layer.
ITU-T recommendation X.800—security architecture for OSI model—defines a systematic approach to assessing and providing security. However, in reality, security is often overlooked and use of security measures in networks is not growing as fast as the number and size of networks. That’s why cyber attacks are becoming so common and easy.
Cyber threat tools are discussed below.
Viruses
A computer virus is a program that spreads from one computer to another by making copies of itself on a computer, or by inserting a piece of computer code into the program or operating system files. It has the capability to replicate itself. Virus attacks can be active or passive type because they can either damage files and/or affect a computer’s performance and stability. A very common example of a virus infecting a computer or spreading is when you open an infected e-mail attachment.
Some e-mail viruses send confidential information in messages when spreading. Others do nothing beyond reproducing themselves. A computer virus may also send a Web address link as an instant message to all the contacts on an infected computer. As soon as this Web address link is accessed, the virus hosted at the link infects the new computer.
John Von Neumann, considered to be the theoretical father of computer virology, designed the world’s first self-reproducing computer program in 1949. Before the proliferation of computer networks, most viruses were only able to spread themselves via removable media, particularly floppy disks. Traditional viruses emerged with the growth of computer networks. In a network system, viruses can increase their chances of replication and spreading to other systems by infecting files on the network file system that is accessed by other computers.
There is no single indicator of a virus infection, but some of the more common symptoms include poor computer performance, pop-up ads displaying even when a pop-up blocker is turned on or the Internet getting disconnected.