Two-thirds of FTSE 350 Board Members Lack Cyber Hack Training
 Some 68 per cent of board members in the FTSE 350 said they have not been trained in responding to a cyber attack, according to the research by accountants KPMG on behalf of the government.
Some 68 per cent of board members in the FTSE 350 said they have not been trained in responding to a cyber attack, according to the research by accountants KPMG on behalf of the government.
While a tenth of FTSE 350 firms do not have a plan in place to deal with cyber incidents, the proportion of businesses that describe it as a top risk has almost doubled in the last three years to reach 54 per cent.
Yet only two per cent of board members said they had received “comprehensive” training, despite the fact that cyber risk has risen rapidly up the agenda after a spate of high-profile hacks and data leaks.
Securing the Network in the Age of IoT
 The recent spate of ransomware attacks has put the spotlight back on network security, making it an uphill battle for almost all organisations in the region. With hackers always trying to get into networks though new and creative ways, the spending on network security, especially on firewalls/UTM products, have gone through the roof.
The recent spate of ransomware attacks has put the spotlight back on network security, making it an uphill battle for almost all organisations in the region. With hackers always trying to get into networks though new and creative ways, the spending on network security, especially on firewalls/UTM products, have gone through the roof.
IDC forecasts worldwide revenues for security-related hardware, software and services will grow to $101.6 billion in 2020. The largest category of investment will be security-related services, which accounted for nearly 45 percent of all security spending last year. Security software is the second largest category, with endpoint security, identity and access management, and security and vulnerability management software driving growth. (Read More)
Building Security into IoT Devices: the New Potential for Security Integration
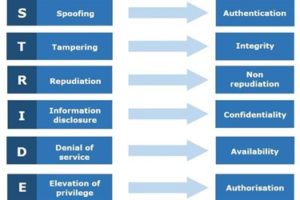 IoT devices, which transmit and receive data and commands over the world’s universal network, are exposed to a far greater variety and number of threats than earlier products that supported machine-to-machine (M2M) communication, typically over a closed, private network.
IoT devices, which transmit and receive data and commands over the world’s universal network, are exposed to a far greater variety and number of threats than earlier products that supported machine-to-machine (M2M) communication, typically over a closed, private network.
The STRIDE threat classification model, originally developed by Microsoft, lists the potential security threats an IoT device or user of that device faces: Spoofing; Tampering; Repudiation; Information disclosure; Denial of service; and Elevation of privilege. (Read More)







