This threat occurs when a person who appears to have sent the e-mail is actually not the person to have sent the e-mail. This can be due to telnetting the SMTP server directly, sharing the e-mail passwords. This threat can be solved by using the concept of public key certificate, with the usage of public key and private key pair, with public key certificate from a certification authority (CA). We should also not allow direct telnetting to the e-mail server and restrict the common password for individual e-mail accounts.
Fig. 4 and Fig. 5 depict the problem of direct telnetting to the e-mail server and sending an e-mail, lacking data origin authentication. In Fig. 4, we are telnetting to an IP address (of the e-mail server) on port 25, which is the default port for SMTP. When writing mail from :< >, we have written impersonator@ipaddress and sent to alice@ipaddress. Whilst retrieval of the e-mail, as shown in Fig. 5, we have telnetted to an IP address (of the e-mail server) on port 110 for the same. When logging on to Alice’s e-mail inbox, we see the mail to have arrived from impersonator@ipaddress. One important point to remember is that we have taken the example as impersonator@ipaddress. This address can be replaced with any other e-mail id and can create lots of problems.
4. Lack of non-repudiation. This threat arises when the receiver cannot trust the contents sent. There is also mistrust that the sender can deny having sent the e-mail.
5. Lack of notification of receipt. Similar to the above situation, there is a threat in which the sender can have a mistrust whether the receiver has received the e-mail or not. The message which was marked as sent may not have been sent.
The last two threats can be removed by the usage of digital signatures. A digital signature is an electronic means of authenticating an online identity. Along with the authentication, it takes care of the non-repudiation and ensures that an actual sender has sent the e-mail and the authentic receiver has received the e-mail. Digital signature is created when we encrypt the hash of the e-mail message with private key of the sender.
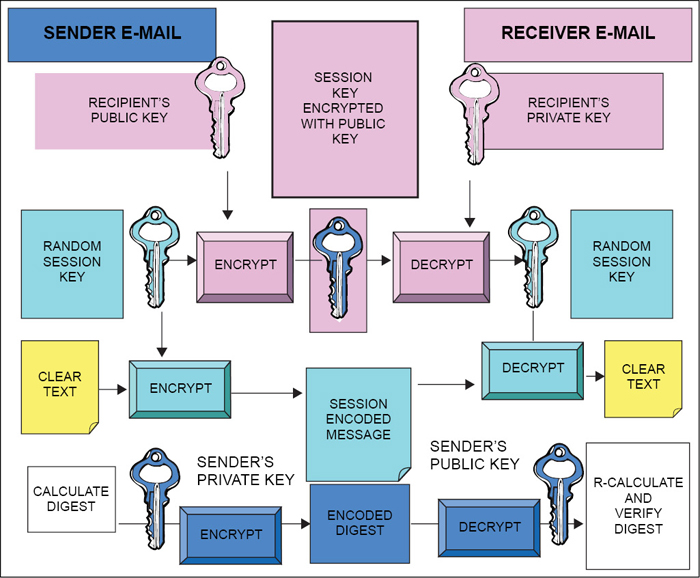
To add to this, we can make this scheme more powerful by encrypting the hash of the e-mail message with the private key of the sender and then again encrypting the result with the public key of the recipient. This ensures that only the receiver is able to read the e-mail and also makes it clear that only the sender has sent the e-mail. This scheme is also known as bidirectional hashing. A fully-secure e-mail can be sent by using the combination of hashing, encryption and digital signature. This scheme is shown in Fig. 6.
Threats to an organisation that arisse due to an e-mail.
These threats mainly include:
1. Disclosure of sensitive information. As we know, disclosure of information can be done quickly by e-mail compared to paper-based mail. The information can be quite sensitive/strategic or of proprietary nature. We do not want to get into the disclosure, whether the disclosure was deliberate (and malicious) or unintentional. Whatsoever it was, disclosure has happened. At the same time, we also have to take into account the fact that disclosure may be internal or external. By external we mean that an e-mail can cross the LAN limit into the Internet world. Such disclosures can lead to loss of information and can even cause loss of reputation of an organisation.
2. Exposure of systems to malicious code. E-mail is the main vector by which computer viruses spread. Self-replicating code embedded in e-mail exploits features/vulnerabilities of the e-mail client. Such vulnerabilities mainly include VBScript, JavaScript in html-formatted e-mail and exe attachments of dancing pigs.
3. Exposure to denial of service attacks. Denial of service (DoS) is an attack which makes a system/individual unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or persons to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. Perpetrators of DoS attacks typically target sites or services hosted on high-profile Web servers such as banks, credit card payment gateways and even root name servers.
One common method of attack involves saturating the target (victim) machine with external communication requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. In general terms, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources so that it can no longer provide its intended service, or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately. These attacks can be in two ways:
(i) Exposure of systems to DoS attacks. E-mail server attached to network may be vulnerable to DoS attacks—more relevant with increasing dependence on e-mail as the communications tool. DoS on mail server may compromise other network services too.
(ii) Exposure of individuals to denial of service attacks. Mail bombing, excessive spam generally exposes an individual e-mail client to DoS attack. Individuals get so spammed by incoming e-mail that they stop reading it. We will deal with e-mail spam and e-mail authentication in the next part.
To be concluded in next part…
The author is working in ADRIN, Department of Space as Scientist ‘SF’ and involved in developing applications on network and data security






