Although security threat can emerge from many sources, the one which is really brutal and catastrophic is terrorism. Terrorism has far reaching consequences like loss of human life and property, and change in behavior pattern of individuals, many of them being irreversible.
Spread of knowledge and education, coupled with strict vigilance, can help contain terrorism and other security threats. However, for robustness in security, electronic threat detection mechanisms are recommended. The main advantage is the passive monitoring by these electronic solutions, which does not impact routine life of any individual and still ensures safety and security. Generally, terrorist attacks are made in densely-populated or sensitive or tourist areas like bus stations, airports, railway stations, hotels, places of worship and other crowded places.
The frequency spectrum is allotted in India by WPC. This means any frequencies used by anyone who is not legally allotted these raise suspicion, and also any illegal activities carried out in the licensed band are suspect. If the illegal and suspicious frequency and its location are determined by any monitoring system, it can help to locate and isolate the suspect without much manual intervention. This technique of detecting and locating the illegal and suspicious RF source is called RF surveillance. Here we discuss the RF surveillance technique which can be used both in preventive and tactical ways to effectively counter terrorist threats.
The need
It is not easy to determine illegal activities in communication and mobile services due to their use en-mass. However, communications between terrorists and anti-social elements can be stopped either by shutting down the network or by jamming all the operating frequencies. This would stop all forms of communications, including security agencies’, and is therefore counter-productive. That is why RF surveillance is required and is gaining popularity, as it enhances security perimeter beyond just physical and visual security.
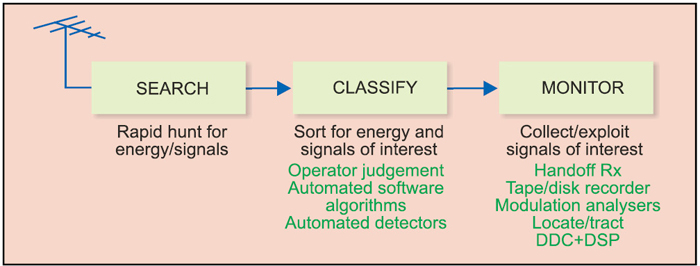

How it works
Radio frequency (RF) surveillance systems must be capable of measuring unknown or unfriendly transmissions and possibly extract the target information content. Direction finding (DF) and geo-location are usually part of RF surveillance signal recovery; also knowledge of the emitter location is offered as part of such systems. The basic block diagram of a generalised RF surveillance system is as shown in Fig. 1.
The three steps that describe it are as below:
Search. Performs the high-speed signal search operation in the selected frequency band and identifies active signals.
Classify. Performs signal classification operation to sort out the signals of interest based on the selected threshold level, alarm conditions and automatic modulation recognition algorithm.
Monitor. On the signal of interest, performs the demodulation and identifies the intelligence available in it. If required, records the signals and the intelligence for further analysis. Once intercepted RF signal is monitored and recorded, the system investigates RF spectrum to identify the target message content.
Who needs it
Surveillance of wireless signals is generally required by spectrum regulators, public safety agencies, border and coastal security, and military intelligence. In the government and military areas, these transmissions are often characterised as signals intelligence (SIGINT). These systems are useful to intercept and locate the different wireless transmitters such as global mobile personal communications by satellite (GMPCS), cellular handsets and VHF/UHF frequency range walkie-talkies. Thus, an RF surveillance system plays a vital role and ensures success in security mission.
Various intelligence and security department personnel like Homeland security department, Border and Coastal Surveillance department, critical infrastructure and perimeter protection forces, signal intelligence groups of Army, Navy and Air Force, technical and aviation research organisations, defence agencies, government end-users, paramilitary forces, regulatory agencies, commercial spectrum monitoring agencies, railways, hospitals, transportation security department, including aviation and maritime transportation, can use these systems.
Overview of use case
Let us define various use cases for RF surveillance systems in different operating environments. Three use cases are stated below:
1. Tactical use case
2. Preventive use case
3. Costal surveillance use case
Note that these are just indicative use patterns, and the RF surveillance system is not limited to these applications.
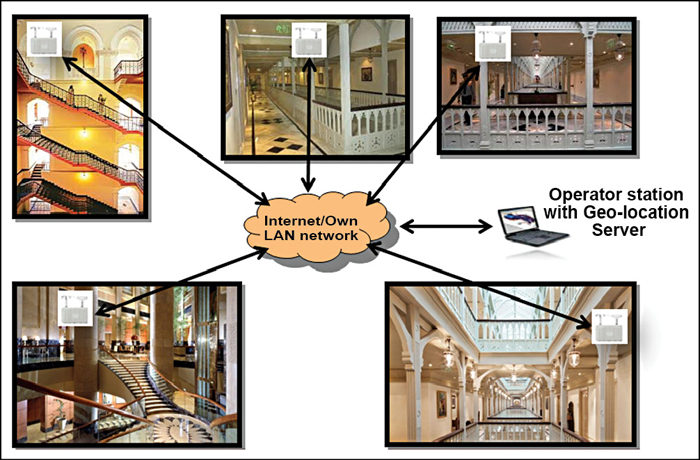
Tactical use case for critical infrastructure protection
RF sensors can be installed in the suspected area around the building as shown in Fig. 2, or RF sensors can be mounted in the sensitive buildings as shown in Fig. 3. All RF sensors can be connected via LAN backhaul either with a wired or wireless system. The sensors can then be time-synchronised and, with its core detection algorithm, the software can detect illegal or threat signal. The system is very easy to install within a few minutes.






