The AuC upon request from the MSC generates a number of security information ‘triplets’—each comprising a RAND, an SRES and a Kc key (the key is generated as part of the triplet but used for encryption rather than authentication). This group of triplets is sent to and stored in the VLR associated with the MS. Each time an authorisation is requested, a new triplet is used. If all triplets held in the VLR are used, the MSC requests a new batch from the HLR/AuC using a “Send Authentication Info” message. The HLR/AuC responds with this information using a “Send Authentication Info Ack” message.
The authentication process is shown in Fig. 2. The subscriber (MS) requests network access by sending its IMSI/temporary mobile subscriber identity (TMSI) to the MSC. The IMSI is sent to the MSC only in the case of first-time entry of the MS into the network or data loss at VLR. The MSC checks whether its VLR holds a valid unused triplet. If not, new pairs are requested from the AuC.
The AuC using the IMSI extracts the subscriber’s Ki. It then generates RAND and applies Ki and RAND to the authentication algorithm (A3) and cipher key-generation algorithm (A8) to produce an authentication SRES1 and a Kc. The AuC then returns an authentication triplet—RAND, SRES1 and Kc—to the VLR.
The MSC/VLR keeps the two parameters—Kc and SRES1—for later use and sends the RAND component of the pair to the MS using an “Authentication and Ciphering Request” message. The MS reads its Ki from the SIM and applies the received RAND and Ki to A3 and A8 to produce SRES2 and Kc. It saves Kc to be used when it receives the command to cipher the channel. The MS returns the generated SRES to the MSC/VLR using an “Authentication and Ciphering Response” message.
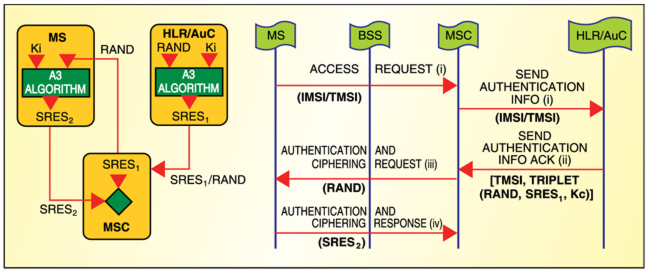
The MSC compares its self-generated SRES1 with that received from the MS. If these are identical (SRES1=SRES2), the user is authenticated and granted access to the network. If these are unidentical (SRES1≠SRES2), all signalling activities are aborted.
User-identity confidentiality.Subscriber identity confidentiality provides for the privacy of GSM subscribers’ identities by ensuring that the IMSI is not disclosed without authorisation. This prevents the intruder from tracing the location of mobile subscribers, gaining information on the resources in use, and matching the user and transmitted signal.
Protection of a subscriber’s IMSI is achieved by issuing a temporary replacement ID known as TMSI. This identity is allocated by the VLR when a subscriber firs affiiates to the network and may be subject to change each time the subscriber reconnects to the network or moves between MSCs (and hence VLRs).
User-data confidentiality (encryption). The confidentiality and privacy of user data on physical connections is achieved by user-data encryption. The encryption prevents the user-data disclosure to unauthorised individuals, entities or processes. GSM recommendations have indicated seven ciphering algorithms and given provision to select one or more algorithms for the mobile station and/or GSM network. The GSM network is responsible for deciding which algorithm to use.
When encryption is requested, the MS signals the network indicating which of the seven ciphering algorithms it supports. The serving network then selects one of these, and signals this to the MS. The selected algorithm is then used by the MS and network. Normally, a standard algorithm (A5) is employed. It is noteworthy that the GSM network has the fexibility not to use encryption in which case-confidentiality is not applied. Th general GSM encryption process is shown in Fig. 3.
Determining the algorithm. After the authentication process, the MS requests the network to establish an encrypted connection. Depending on the priorities, the A5 algorithm (or any other algorithm selected by the network) is first negotiated. The priorties are:
1. If the MS and the network have no common versions of the A5 algorithm and the network and/or the MS is not prepared to use an unencrypted connection, the connection is released.
2. If the MS and the network have at least one version of the A5 algorithm in common, the network selects one of the mutually acceptable versions for use on that connection.
3. If the MS and the network have no common versions of the A5 algorithm and the network is willing to use an unencrypted connection, an unencrypted connection is es-tablished.
Kc key generation. The Kc key is generated at both the MS and the AuC by applying the cipher key-generation algorithm (A8) to RAND (generated by the AuC) and Ki—unique to each MS. Kc key generated at the AuC is passed to the MSC/VLR along with RAND and SRES as part of each triplet.
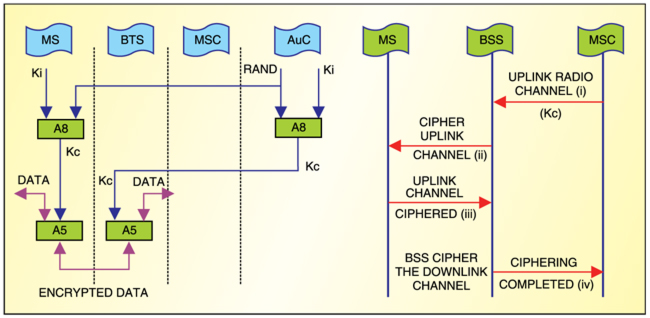
Ciphering. Encrypted data is produced by passing the Kc key, and the clear user-data through A5 algorithm is stored in the MS and BSS. The transition from clear mode to ciphered mode proceeds as follows:
1. The MSC/VLR requests the BSS to cipher the radio channel. Included in this message is Kc, which was made available earlier during the authentication process.
2. The BSS retrieves Kc from the message and transmits a clear “Start Cipher” message to the MS requesting it to start ciphering the uplink channel.
3. Once this message is received correctly, enciphering and deciphering start on the MS side.
4. Enciphering on the BSS side starts as soon as synchronisation is achieved and an encrypted MS-generated frame or a message is correctly deciphered at the BSS. The BSS upon ciphering the downlink channel sends a “Cipher Complete” message to the MSC.
Protection of signalling information. In order to ensure the confidetiality of user-related signalling data exchanged between the MS and BTS, the encryption of signalling data is done. Signalling information elements like IMSI, IMEI and calling/called sub-scriber directory number are protected whenever used after initial connection establishment.
The author is a junior telecom officer at Bharat Sanchar Nigam Ltd (BSNL) pursuing PhD in electronics engineering from Institute of Technology, Banaras Hindu University, Varanasi







