A physical unclonable function(PUF) is a function that is embodied in a physical structure and is easy to evaluate but hard to predict. Further, an individual PUF device must be easy to make but practically impossible to duplicate, even given the exact manufacturing process that produced it. Rather than embodying a single cryptographic key, PUFs implement challenge–response authentication. When a physical stimulus is applied to the structure, it reacts in an unpredictable way due to the complex interaction of the stimulus with the physical microstructure of the device. This exact microstructure depends on physical factors introduced during manufacture which are unpredictable(like a fair coin). The applied stimulus is called the challenge, and the reaction of the PUF is called the response. Unlike a ROM containing a table of responses to all possible challenges, which would require hardware exponential in the number of challenge bits, a PUF can be constructed in hardware proportional to the number of challenge and response bits.
What is ‘unclonability’?
Unclonability means that each PUF device has a unique and unpredictable way of mapping challenges to responses, even if it was manufactured with the same process as a similar device, and it is infeasible to construct a PUF with the same challenge–response behavior as another given PUF because exact control over the manufacturing process is infeasible. This is because a response is created by a complex interaction of the challenge with many or all of the random components. The combination of the physical and mathematical unclonability renders a PUF truly unclonable.
NXP Semiconductors today announced that it will be the first company to bring to market smartcard and embedded secure element chips that integrate Intrinsic-ID’s industry-leading PUF (Physically Unclonable Function) technology. As explained above, PUFs are an innovative way of safeguarding individual chips from data theft by using the unique ‘fingerprint’ inherent in every semiconductor device to protect its encryption key, making it very hard to clone and thus reverse-engineer and compromise security micro-controllers.
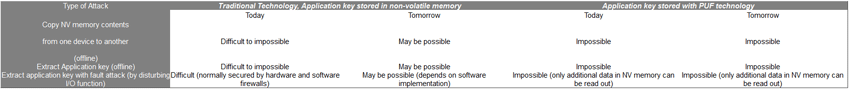
Types of attacks
The Smart Card industry typically places attacks in one of three categories:
Side channel attacks (non-invasive attacks) – such as using information out of the power profile or the electromagnetic emanation
Fault attacks (semi-invasive attacks) – such as disturbing the IC by applying laser light or a voltage glitch
Reverse engineering (invasive attacks) – reverse engineering parts of the IC, possibly combined with probing signals
Typical reverse engineering attacks on Smart Card ICs include the following:
- Reverse engineering of a functional block
- Reverse engineering of parts of the IC as preparation for a subsequent probing attack
- Extracting memory content
Standard Counter-measures
The standard counter-measures taken against reverse engineering attacks include the following:
- Memory encryption
- Encryption of data
- Scrambled logic (especially no hard macros)
- No logic relevant to security in top metal layers
Global trends such as urbanization, digitization of governmental documents, improved banking security and growing NFC adoption means that security chips are being adopted more than ever to protect user data, credentials and finances. In parallel, more sophisticated attacks have been developed that attempt to undermine security chip functionality and steal this information. By integrating Intrinsic ID’s PUF technology into its secure microcontroller SmartMX2, NXP significantly enhances the chip’s security architecture and strengthens applications such as NFC-enabled mobile payment, electronic ticketing, and eGovernment and cyber security services. NXP has shipped almost two billion SmartMX chips to its customers including 86 out of 102 countries with ePassport projects.








