Fuzzing testing. Fuzzing is a type of negative testing that involves injecting unexpected, random data as an input to the application, to test the behaviour of application under random data. Fuzzing is used to find security loopholes in operating system, software, web application and coding errors.
Cross-site request forgery. Also known as a one-click attack or session riding, and abbreviated as CSRF or XSRF, it is a type of malicious exploit of a website whereby unauthorised commands are transmitted from a user that the website trusts.
Insecure direct object reference. It occurs when an application exposes an internal implementation object to the user. Some examples of internal implementation objects are database records, URLs or files. An attacker can modify the internal implementation object in an attempt to abuse the access controls on this object.
Comparison of security testing tools
In order to compare the representative testing tools, we consider the sample of web application Jammu and Kashmir Employment System. The system aims to immediately provide the facility for citizens to submit online form for the services identified by the state of Jammu & Kashmir. Subsequently, the citizen must be able to check the status of his/her application online. These submissions and status tracking can be done through the Common Service Centres (CSCs) or through the J&K State Portal directly.
Jammu and Kashmir Employment System will help the government of Jammu & Kashmir in creating an integrated information infrastructure that will expand, integrate and enhance the utility and reach of the services provided by the government by utilising the network of the CSCs. The state-portal is envisioned as an informative, interactive, integrated and trusted service delivery channel for the government to citizens (G2C) and government to business (G2B) services of the state and the government’s constituent departments. The SSDG acts as hub (standards-based messaging switch) for all the interactions and seamless interoperability across service seekers (the citizens and businesses) and various service providers (government departments) and even among government departments.
To test the representative tools, we configured each tool to run the test. The configuration included installation, setting up test parameters, test data, result analysis, etc.
We ran the test on the machines. Configuration for the machine was Intel core i3-3110M 2.40GHz processor with 2GB RAM, running Microsoft Windows. The tests were conducted two times a day to minimise the effect of the Internet connection on test results and to obtain accurate measurements.
Overview of tools
Wapiti. Wapiti is a web application vulnerability scanner that was created in 2006 by Nicolas Surribus. It does not scan the source code of the application but scans the web pages of the launched web application. Wapiti acts like a fuzzer and injects payloads to see if a script is vulnerable. Wapiti can detect lots of vulnerabilities, such as file-handling errors, database injection, cross-site scripting, LDAP injection and CRLF injection. Wapiti is easy to use, open source and the user does not need security knowledge. But it is not able to find all the vulnerabilities.
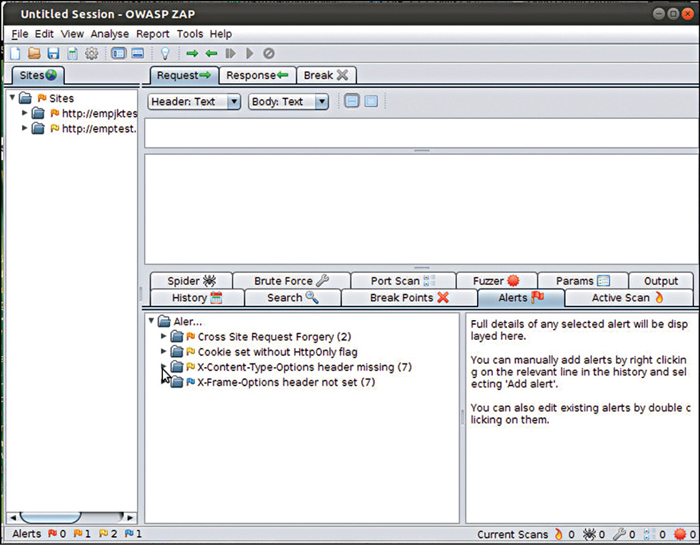
OWASP ZAP. OWASP ZAP is a penetration-testing tool which comes with plenty of features. Its main features is active scanning which is used to find certain kind of vulnerabilities, including XSS and others, except some logical vulnerabilities that can never be found by any automated security testing tool. Another interesting feature of ZAP is fuzzing. ZAP provides a list of fuzzers with the help of which we can fuzz any part of the application. This tool is open source, easy to use, well organised and up-to-date. High false positive factors and zero support for multiple scanning profiles are its main disadvantages.
Netsparker Community Edition. Netsparker is a free web application security scanner. It helps the developers who want to scan their web applications instantly and find the vulnerabilities. Netsparker Community Edition scans for SQL injection, XSS, Boolean SQL injection, backup files and static tests. It scans all types of web applications without limiting itself to technology or platform they are built on. It supports Javascripts/AJAX, can show impact of vulnerabilities or remedy for that vulnerability.
Tools results and analysis
The web application was tested using the three tools OWASP ZAP, Wapiti and Netsparker Community Edition. The test results obtained using these tools were:
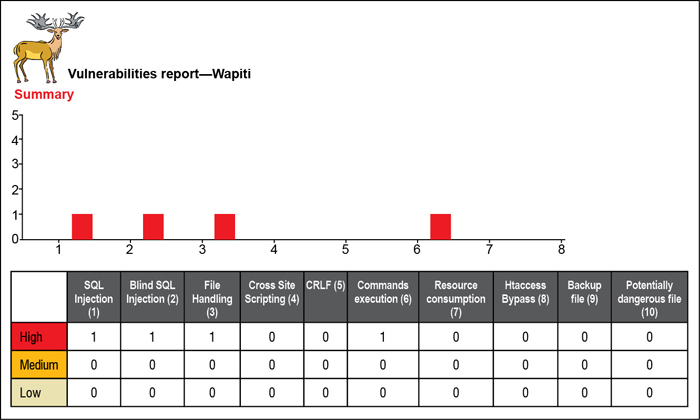
Testing results with Wapiti. Using Wapiti, the following four vulnerabilities were discovered in the Jammu & Kashmir application (the number in brackets refers to the number of occurrence of the vulnerability):
SQL injection (1): SQL injection is a technique that exploits a vulnerability occurring in the database of an application. It is a code injection that can allow the tester to read sensitive information from database and to modify it. SQL Injection occurs when input contains escaped characters, or user input is not strongly typed.