A recent false report in newspapers about breach of data at Indian Registry for Internet Names and Numbers (IRINN) caused a huge turmoil both at national and international levels. A lot of government organisations came under the scanner. The incident questioned validity of the entire digitisation movement.
With all the government data being processed smartly by cloud technology, the possibility of exposure at every point and theft has increased. Various government agencies including Unique Identification Authority of India (UIDAI) have issued statements reiterating the safety of their databases.
Such incidents are on a rise. Globally, securing the ways in which machine communication takes place is top priority. Data breach and hacking is becoming an increasing concern as everything that we do now-personal or professional-is all about data and system communication.
Allaying such fears, Arvind Gupta, head of #DigitalBJP and co-founder of Botworx.ai, said, “Today, Apple is the most valuable company in the world by virtue of the consumer data that it claims to own and its intellectual property. The Indian government’s IT and cloud infrastructure is one of the finest in the world and robust enough to secure citizens’ data end-to-end in a way that is leak-proof and uses the best consent architecture.”
Peter Gartenberg, general manager, Enterprise Commercial, Microsoft India, shared, “The Internet of Things (IoT) is the wave of the future, offering enterprises immediate and real-world opportunities to reduce their costs, increase revenue and transform business. However, concerns about security, privacy, compliance and transparency remain with regards to IoT infrastructure and merging of the cyber and physical worlds. Several measures are already being taken to bridge gaps and prevent security breaches at the device level. Efforts are being made to tackle obstacles before they come up.”
Gartner states that the IoT has made digital presence pervasive in institutions and further among mankind as a whole. New participants of the framework are data scientists, integrators and vulnerable endpoints. Technology decision makers must make choices for future advancement considering risk to privacy and security.
To understand the criticality of security in the IoT, one must consider the various components within the IoT architecture as working together with each other and not in silos.
William E. Lamie, president, Express Logic, Inc., said, “With edge nodes and connected devices rapidly populating the IoT landscape, the need to put an end to security breaches of sensitive and confidential information has never been more critical.”
Threats we face
Narang Kishor, principal design architect, Narnix Technolabs, explained, “The IoT paradigm is all about connecting everything that exists with everything else. The IoT is a neural network of globally aware, intelligent and heterogeneous devices connected with each other in multiple ways to solve some problems of the society.”
“The problem stems when we go overboard with it, like we have, and there is no control mechanism. Earlier, technologies like supervisory control and data acquisition (SCADA) and remote sensing worked in a controlled environment. Now, the applications have opened up to almost every product or service. Applications like smart home and smart healthcare are on-board the IoT. Larger concepts like Smart Cities further add to the complexity. With public Wi-Fi, anybody can connect with anything in the locality because the infrastructure is automated and intelligent.
“Excessive penetration of such technologies also brings about many potential risks. For example, every functioning device is electricity dependent. The moment there is a power failure, life comes to a standstill. On the Smart City network, if the security isn’t strong enough, a hacker can access your critical centres and bring the entire nation to a standstill. Today, we don’t need a nuclear bomb to destroy a nation, we just need a few good hackers to bring down its power and communication and the nation would be on its knees. A few months ago, Russian hackers used Chinese webcams to attack American servers.”

Divyang Hemnani, engineer-embedded systems, Infinium Solutionz, added, “Hackers steal data by infecting the software of IoT devices. They use this infection to modify firmware in the devices. Consequently, all the data can be linked with the hacker’s server. Due to the depth of software hacks, people are generally unable to recognise the security vulnerability of their devices.”
Sharing his views on the vulnerabilities of IoT systems, Parag Sharma, CEO, Mantra Labs, said, “Security keys are at times used to authenticate the code being executed on an embedded device, or to authenticate the connection from an IoT device to the server. In the event of a security key being compromised, a hacker may be able to intrude into the device and run an unintended malicious code. This is entirely unwanted, and exposes users to serious consequences. Unintended behaviour of a device, and mounting hack attempts from these devices are the threats being faced. While it may not be disastrous for some IoT devices for entertainment to malfunction, a critical life-saving device or a device of strategic importance going haywire can have disproportionate losses associated.”
Major layers of IoT architecture
An IoT system consists of a complex multi-tiered architecture, with connectivity and security at the fulcrum of the setup. It includes the following significant layers:
Edge device and components layer
This layer consists of components like sensors, actuators and controllers embedded in or connected to the devices present in the field or at the edge. In this layer, the data is actually generated, evaluated and digitised.
Network or transport layer
Data digitised in the edge layer is transferred to the central cloud server through gateways. Connected application devices can access the data from the cloud. The cloud provides a Platform as a Service (PaaS), where the data is stored and analysed.
End application layer
This tier constitutes the operational application on the user device (smartphone, computer, smartwatch, etc). It displays and represents data captured by the sensors and shares over the cloud.
Standards to ensure IoT security
Dr Rishi Mohan Bhatnagar, president, Aeris India, and chairperson of The Institution of Engineering and Technology – IoT panel for India, said, “When it comes to IoT security, three aspects need attention-sensors, network and applications. With billions of devices coming online, we now have that many more vulnerabilities created, even if we ignore the permutations and combinations. To address the challenge, we need to have a well-etched IoT security policy and framework crafted and deployed. We also need to ensure that these policies are adhered to at all times.”
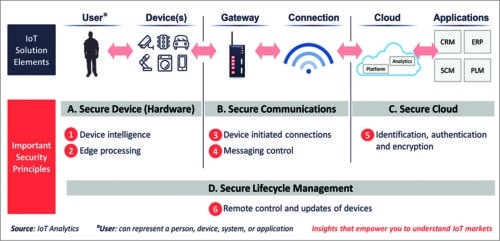
The IoT is adopting newer protocols like Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP) due to their specific advantages. Peter Carbone, vice president and general manager of Synergy IoT Platform Business Division, Renesas Electronics Corporation, explained, “For transport, TCP/IP network software protocols are the standard. But the challenge is to support them in constrained IoT devices that are typically MCU-based as they get closer to the edge where power, cost and space are limited. A number of newer connectivity protocols have been developed over recent years that target these constrained devices. One of these protocols is MQTT using TCP with a publish-subscribe messaging pattern to reduce the volume of network traffic, improve power efficiency and decouple data exchange timing of connected objects on the network.” However, these standards need to be coupled with security protocols for effective safety. Expressing his concern, Sharma said, “The 802.11 Wi-Fi protocol has shown to be susceptible to denial-of-service (DoS) and man-in-the-middle (MiM) attacks as well as to cracking of the secret key.” Talking about the standards of data encryption systems, Hemnani said, “Today’s strong encryption and authentication schemes are based on cryptographic suites such as Advanced Encryption Suite (AES) for confidential data transport, Rivest-Shamir-Adleman for digital signatures and key transport, and Diffie-Hellman for key negotiations and management.” Transport Layer Security (TLS) standard is widely used for data-transport-level security.
Latest security measures
IoT security majorly revolves around data generated in the system and its circulation within the system. End application layer, transportation layer and field devices with embedded components play a big role in IoT security as most data transactions happen in these regions. IoT data security is largely managed with the help of cryptography algorithms, digital signatures and security certificates.
Security in transport and connectivity layer
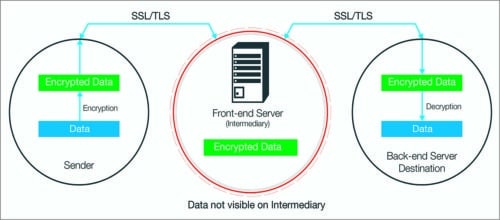
In legacy IoT systems, Hypertext Transfer Protocol (HTTP) with secure encryption has been the common safety standard. However, it is data-intensive and comparatively slow. To mitigate these drawbacks, MQTT has become the more preferred IoT protocol layered above the transport tier. It is simple and fast with low code-footprint. These characteristics make it more suited for remote location connection or low-bandwidth actions. MQTT comes with its own set of security measures. However, these measures still leave the network vulnerable. So the trend in securing the transport layer is to secure the MQTT protocol with Secure Socket Level (SSL) certification. The most advanced version, SSL 3.0 certificate, is applied at the cloud server side as well as the mobile and devices side, encrypting communication within the network. A newer option for network security is the Transport Layer Security (TLS) 1.2 certificate. TLS, successor to SSL, has quickly picked up prominence with certain advantages over SSL, such as like better compatibility with newer browsers. Carbone shared, “For secure operation, IoT devices must protect data (and code) at rest on them, as well as data in motion. The TLS cryptographic protocol is widely used to secure data in motion by three ways: by establishing secret keys between the client and server, applying hashing algorithms to detect alteration or forgery of packet content, and establishing remote host identity using digital certificates.” For example, The Synergy IOT Software Package v.3.1.0 of Renesas Energy Corporation integrates with Express Logic’s NetX Security suite that incorporates TLS protocol for socket-layer security.
Securing the data itself
Data stored over the server is encrypted using AES security. The 128-bit AES is a strong data-encoding standard. Established by the National Institute of Standards and Technology, it works on the substitution-permutation algorithm of splitting the data in a block size of 128 bits and encrypting it with a 128-bit key length. Major businesses, including banks and financial services, use 128-bit AES data encryption.
Securing device access to the server
To grant end-users application access to the server using their mobile/computer device, the main security measures revolve around user and device authentication. OAuth 2.0 is the most used authorisation and authentication framework. It is being used by firms like Google and Facebook. MQTT protocol supports the following authentication processes:
1. Username and password or access token
MQTT protocol develops a UTF-8 encoded string user name and a binary data-type password, where each field can be expanded up to 65,535 bytes maximum. The client, i.e., the user, needs to provide a valid username and password to get access from the MQTT broker. Many systems accept passwords instead of tokens, using which the broker can assess the validity, signature and access rights of the user.
2. One-time password (OTP)
It is often used for a two-step security, wherein registered devices need to verify their eligibility of access based on an OTP received on the device.
3. Biometrics
This mode of authentication is gaining popularity. Many smartphones and smart devices have introduced fingerprint scanners for access. IoT systems are also incorporating biometric authentication procedure to improve the security measures. Some of the newer bio-authentication processes include facial scan and eye scan. Hemnani informed, “Like smartphones, IoT devices will also implement fingerprint sensor soon. That way, only an authorised user will be able to access the IoT device.”
Security at the edge and component level
Field devices where the data is being generated by the sensors have a temporary storage capacity, which queues the data to be pushed to the server. The major security threats that device storage faces include tampering of the telemetry data, tampering of the cached content and alteration of the device operating system. Simple security options include digital signatures, message authentication code (MAC) and resource access control. Dr Amarjeet Singh, co-founder and CTO, Zenatix Solutions, explained the process of securing a server from a rogue edge device which might have been physically taken over by a hacker: “A rogue device intruding into an IoT system tries to overload the server by sending an abnormally high amount of data. A security measure taken for server configuration is to limit the amount of data package the server will accept from each device at a given time interval. If any device is transacting higher data than the threshold too often, it is barred from the network.” Device gateways that channel sensor data to the server can be secured by BitLocker. Talking about securing the data in embedded components, Kumar Bhaskar, technology lead of Beyond Evolution, a company working on IoT devices, said, “Components of IoT systems use very limited resources in the form of embedded hardware like a small chip, sensor, controller and RAM. So data is embedded in the controller’s memory in encoded or symbolic format. Once the microcontroller is coded, it is locked. So, firstly the data cannot be fetched by any means from the controller. Additionally, the data itself will not be in a readable format.”
Software as security suites
Implementing security software has been a staple safety procedure for IoT systems. Here, Sharma shared, “Mostly software solutions are available to secure firmware.” Gartenberg added, “Success of this transformation largely depends on choosing the right IoT software and service provider who can not only catalyse this transformation by understanding business needs but also provide services and software built with security and compliance as major design considerations.” Talking about Microsoft’s contribution to IoT security via software, he added, “The Microsoft Azure IoT Suite builds in security measures by design, enabling secure asset monitoring to improve efficiencies, drive operational performance to enable innovation, and employ advanced data analytics to transform businesses. With its layered approach towards multiple security features, and design patterns, Azure IoT Suite helps deploy an infrastructure that can be trusted by any business.” 
What’s the future
In the coming two to three years, even newer security upgrades will be available and the systems will have to be updated. Code signing abilities with higher levels of encryption may be a step forward to secure the devices.
As regards security practices for the IoT, Dr Bhatnagar said, “A security operations centre needs to be established to monitor threats in a proactive manner while detecting and tracking signatures of divergent activities. On the tactics side, sanitise your operational environment by deploying patches, keeping segmented offline back-ups, conducting audits and deriving visibility into your core and peripheral networks. If a malware breaches your first layer of defence, you should be able to know where it is and what exactly it is doing. Most importantly, ensure that everyone in your organisation understands the collective responsibility they bear for cybersecurity.” Experts feel that endpoint security monitoring will see the maximum advancements in the next ten years. Data analytics, machine learning and artificial intelligence will play a big role in the prediction of attacks and suspicious activities. The current movement towards a common IoT standard will influence the future security trends. We will see better encryption capabilities and more evolved authentication and authorisation processes.






