In today’s fast-paced lifestyle, consumers want communication at faster speed and lower cost, more broadband capabilities as well as nomadic and mobility support. Keeping these demands in mind, IEEE 802.16 working group has come up with a new wireless communications standard called the broadband wireless access (BWA). Commonly known as WiMAX (worldwide interoperability for microwave access), this is a fast evolving technology used to form wide-range wireless networks with high data rate of information transfer.
We live in a variety of networking environments for using Internet-based services and applications. Data security becomes an important issue in such interconnected networks in order to safely transmit or receive information. Due to this, different security protocols are designed and deployed with network standards.
The latest update given by WiMAX Forum—the IEEE 802.16m—claims to offer up to 100Mbps mobile and 1Gbps fixedspeeds. The update is added to the WiMAX standard in both its versions—fixed(IEEE 802.16d-2004) and mobile (IEEE 802.16e-2005) broadband wireless access.
WiMax protocol
IEEE 802.16 standard essentially specified two aspects of the air interface for WiMAX—the physical layer (PHY) and the media access control layer (MAC) (refer Fig. 1). The physical layer defnes electrical and physical specification for devices, establishment and termination of a connection to a communication medium, communication flow control, modulation, coding, etc. On the other hand, MAC layer is further divided into three sub-layers—convergence, common part, and security or privacy.
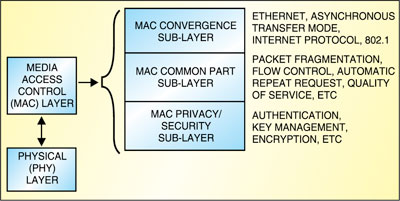
The convergence sub-layer de-scribes how wireline technologies such as asynchronous transfer mode (ATM), Ethernet, 802.1 (LAN/MAN) and Internet protocol (IP) are encapsulated on the air interface and how data is classified.The common part sub-layer is responsible for idle-mode processes like cell selection, paging structures and location-area updates. This layer is also responsible for sleep-mode processes, handover procedures, multicast and broadcast services, quality-of-service (QoS) class and automatic repeat request (ARQ) processes. It also does header suppression, packing and fragmentation for efficient use of spectrum.
The security sub-layer provides subscribers with privacy, authentication or confidentiality across the broadband wireless network. It is accomplished by applying crypto-graphic transforms to MAC packet data units carried across connections between the subscriber station and the base station. Secure communications are delivered by using secure key exchange during authentication, and encryption using advanced encryption standard (AES) or data encryption standard (DES) during data transfer. The MAC layer incorporates privacy key management version 2 (PKMv2) for MAC layer security. PKMv2 incorporates support for extensible authentication protocol (EAP).
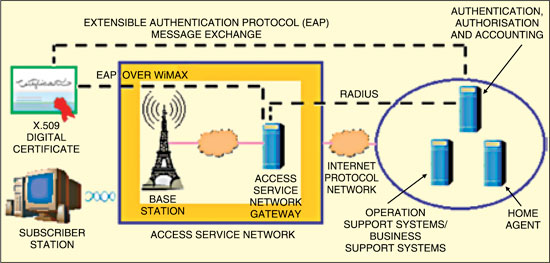
In addition, the security sub-layer provides operators strong protection from theft of service. The base station protects against unauthorised access to data transport services by securing the associated service flowsacross the network. The security sub-layer employs an authenticated client/server key management protocol in which the base station server controls distribution of keying material to the client subscriber station. Additionally, the basic security mechanisms are strengthened by adding digital certificate-basedsubscriber station device authentication to the key management protocol.
Security components
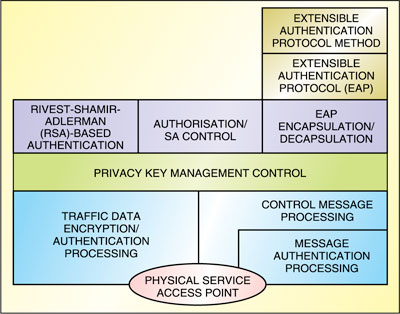
WiMAX security uses two component protocols—encapsulation protocol and privacy key management (PKM) protocol. The encapsulation protocol is used for securing packet data across the wireless network. This protocol defines a set of supported cryptographic suites, i.e., pairings of data encryption and authentication algorithms and the rules for applying these algorithms to a MAC packet data unit payload.
On the other hand, the PKM protocol is used for secure distribution of keying data from the base station to the subscriber station. Through this key management protocol, the subscriber station and the base station synchronise keying data. In addition, the base station uses the protocol to enforce conditional access to network services. The stack of security components of the system is shown in Fig. 2.
Key management protocol. There are two PKM protocols supported in IEEE Standard 802.16—PKM version 1 (PKMv1) and PKMv2 with more enhanced features such as new key hierarchy, advanced encryption standard (AES)-cipher message authentication code, AES-key-wraps, and multicast and broadcast services. PKM protocol allows mutual authentication, unilateral authentication, periodic re-authentication/re-authorisation and key refresh.
Key management protocol uses either extensible authentication protocol, or X.509 digital certificatestogether with Rivest-Shamir-Adlerman (RSA) public-key encryption algorithm or a sequence starting with RSA authentication and followed by extensible authentication protocol authentication. It uses strong encryption algorithms to perform key exchanges between a subscriber station and base station. RSA protocol support is mandatory in PKMv1 but optional in PKMv2. However, extensible authentication protocol support is optional in both the versions of key management protocol, unless specifically required.
PKM’s authentication protocol establishes a shared secret, called authorisation key, between the subscriber station and base station. The shared secret is then used to secure subsequent PKM exchanges of trafficencryption keys. This two-tiered mechanism for key distribution permits refreshing of trafficencryption keys without incurring the overhead of computation-intensive operations.
The authorisation key is derived by the base station and subscriber station from the pre-authorisation key (in case of RSA-based authorisation procedure) and/or the PMK (in case of extensible authentication protocol-based authorisation procedure). The exclusive-or (XOR) value of primary authorisation key and pairwise master key is mainly used to generate the authorisation key. The Dot16KDF algorithm is used for authorisation key derivation.
The base station authenticates a client subscriber station during the initial authorisation exchange. Each subscriber station presents its credentials, which is a unique X.509 digital certificateissued by the subscriber station’s manufacturer (in case of RSA authentication) or an operator-specified credential (in case o EAP-based authentication).
The base station associates the subscriber station’s authenticated identity to a paying subscriber and hence to the data services that the subscriber is authorised to access. Thus, with the authorisation key exchange, the base station determines the authenticated identity of a client subscriber station and the services (i.e., specifictrafficencryption keys) the subscriber station is authorised to access. Since the base station authenticates the subscriber station, it may protect against an attacker employing a cloned subscriber station masquerading as a legitimate subscriber.
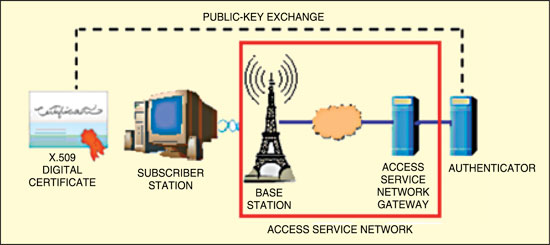
Privacy key management RSA authentication. The PKM RSA authentication protocol uses X.509 digital certifcates—the RSA public key encryption algorithm that binds public RSA encryption keys to MAC addresses of subscriber stations. The digital certificat contains the subscriber station’s public key and MAC address. When requesting an authentication key, a subscriber station presents its digital certificateto the base station. The base station verifies the digital certificateand then uses the verifiedpublic key to encrypt an authentication key, which the base station then sends back to the requesting subscriber station (refer Fig. 3).
All subscriber stations using RSA authentication have factory-installed RSA private/public key pairs or provide an internal algorithm to generate such key pairs dynamically. If a subscriber station relies on an internal algorithm to generate its RSA key pair, it generates the key pair prior to its firstauthorisation key exchange. All subscriber stations with factory-installed RSA key pairs also have factory-installed X.509 certificates.
PKM extensible authentication protocol authentication. This authentication uses extensible authentication protocol (EAP) in conjunction with an operator-selected EAP method (e.g., EAP-transport layer security (TLS) or EAP-tunnelled TLS with Microsoft challenge handshake authentication protocol version 2 (TTLS MS-CHAPv2)). The method uses a particular kind of credential—X.509 certificate in case of EAP-TLS, o a subscriber identity module in case of EAP-SIM (refer Fig. 4).
EAP authentication provides dynamic encryption keys to wireless users. These are more secure than static encryption keys. If an intruder passively receives enough packets encrypted by the same encryption key, he can perform a calculation to learn the key and use it to join a network. Because dynamic encryption keys change frequently, these prevent intruders from performing the calculation and learning the key.
After successful EAP-based authorisation, if the subscriber station or base station negotiates authorisation policy as ‘authenticated EAP after EAP’ mode, the authenticated EAP messages carries the second EAP message. It cryptographically binds previous and following EAP authentication sessions, while protecting second EAP messages. In order to prevent ‘man-in-the-middle attack,’ the firstand second EAP methods should fulfil the mandatory criteria.
During re-authentication, the EAP transfer messages are protected with a hashed message authentication code or cipher message authentication code protocol. The base station and subscriber station discard unprotected EAP transfer messages or EAP transfer messages with invalid hashed message authentication code or cipher message authentication code digests during re-authentication.
Message authentication code keys are used to sign management messages in order to validate the authenticity of these messages. The message authentication code to be used is negotiated at a subscriber station’s basic capabilities negotiation request. There are different keys for uplink and downlink messages. For a multicast message (in down-link only) and for a unicast message, a different message authentication key is generated. In general, message authentication keys used to generate the cipher message authentication code value and the hashed message authentication code-digest are derived from the authorisation key.
Cryptographic method of data encryption
Encryption services are defined as a se of capabilities within the MAC security sub-layer. Encryption information is allocated in the generic MAC header format and applied to the MAC packet data unit payload when required by the selected ciphersuite while the generic MAC header is not encrypted.
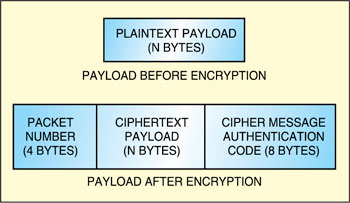
With advanced encryption standard’s counter with cipher block chaining-MAC mode (an authenticated encryption algorithm designed to provide both authentication and confidentiality),the packet data unit payload (after encryption) has a format as shown in Fig. 5. Here packet data unit payload is prepended with a 4-byte packet number. The packet number is transmitted with the least significantbit firstand the packet number itself is not encrypted. The packet number associated with a security association is set to ‘1’ when the security association is established and a new trafficencryption key installed. After each packet data unit transmission, the packet number is incremented by ‘1.’
On uplink connections, the packet number is XORed with 0x80000000 prior to encryption and transmission. On downlink connections, the packet number is used without such modifiction. The ciphertext message authentication code is transmitted such that byte index ‘0’ is transmitted firstand byte index ‘7’ transmitted last.
The result
WiMAX users should feel confdent that their transmitted data is free from eaves-dropping or manipulation and only authorised users can access WiMAX services. The improved WiMAX technology implements improved security architecture. Thus the operator ensures that only authorised subscribers access the network and use appropriate services subscribed by them.
The author is a research scholar pursuing Ph.D in electronics engineering from Indian Institute of Technology, Banaras Hindu University (IIT-BHU), Varanasi